A company recently experienced a data breach and the source was determined to be an executive who was charging a phone in a public area. Which of the following would most likely have prevented this breach?
The primary goal of the threat-hunting team at a large company is to identify cyberthreats that the SOC has not detected. Which of the following types of data would the threat-hunting team primarily use to identify systems that are exploitable?
A large financial services firm recently released information regarding a security breach within its corporate network that began several years before. During the time frame in which the breach occurred, indicators show an attacker gained administrative access to the network through a file downloaded from a social media site and subsequently installed it without the user's knowledge. Since the compromise, the attacker was able to take command and control of the computer systems anonymously while obtaining sensitive corporate and personal employee information. Which of the following methods did the attacker most likely use to gain access?
A company is adding a clause to its AUP that states employees are not allowed to modify the operating system on mobile devices. Which of the following vulnerabilities is the organization addressing?
A vulnerability has been discovered and a known patch to address the vulnerability does not exist. Which of the following controls works best until a proper fix is released?
A systems administrator set up an automated process that checks for vulnerabilities across the entire environment every morning. Which of the following activities is the systems administrator conducting?
A company is designing the layout of a new data center so it will have an optimal environmental temperature Which of the following must be included? (Select two).
Which of the following test helps to demonstrate integrity during a forensics investigation?
A security administrator received an alert for a user account with the following log activity:
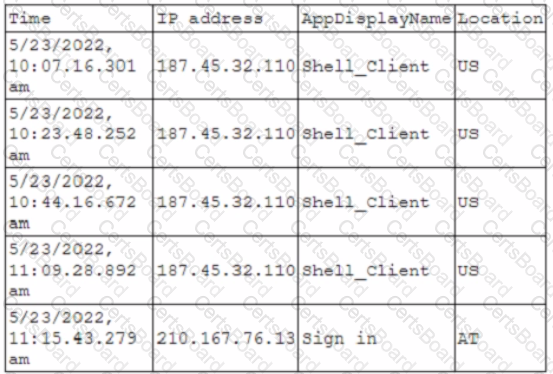
Which of the following best describes the trigger for the alert the administrator received?
After reviewing the following vulnerability scanning report:
server:192.168.14.6
Service: Telnet Port: 23 Protocol: TCP Status: Open Severity: High
Vulnerability: Use of an insecure network protocol
A security analyst performs the following test
nmap -p 23 192.1€8.14. € --script telnet-encryption
PORT STATE SERVICE REASON
23/tcp open telnet syn-ack
I telnet encryption:
| Telnet server supports encryption
Which of the following would the security analyst conclude for this reported vulnerability7?
Which of the following is a solution that can be used to stop a disgruntled employee from copying confidential data to a USB drive?
A security engineer must deploy two wireless routers in an office suite Other tenants in the office building should not be able to connect to this wireless network Which of the following protocols should the engineer implement to ensure the strongest encryption?
A company is working with a vendor to perform a penetration test. Which of the following includes an estimate about the number of hours required to complete the engagement?
A company located in an area prone to hurricanes is developing a disaster recovery plan and looking at site considerations that allow the company to quickly continue operations. Which of the following is the best type of site for this company?
An enterprise is trying to limit outbound DNS traffic originating from its internal network. Outbound DNS requests will only be allowed from one device with the IP address 10 50 10.25
Which of the following firewall ACLs will accomplish this goal?
Which of the following considerations is the most important for an organization to evaluate as it establishes and maintains a data privacy program?
A security administrator is analyzing the corporate wireless network. The network only has two access points running on channels 1 and 11. While using airodump-ng. the administrator notices other access points are running with the same corporate ESSID on all available channels and with the same BSSID of one of the legitimate access points. Which of the following attacks is happening on the corporate network?
Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to coiled network traffic between workstations throughout the network The analysts review the following logs:
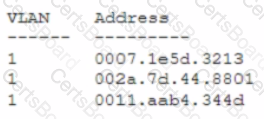
The Layer 2 address table has hundreds of entries similar to the ones above Which of the following attacks has most likely occurred?
A security analyst discovers several jpg photos from a cellular phone during a forensics investigation involving a compromised system The analyst runs a forensics tool to gather file metadata Which of the following would be part of the images if all the metadata is still intact?