A security researcher has alerted an organization that its sensitive user data was found for sale on a website. Which of the following should the organization use to inform the affected parties?
Which of the following function as preventive, detective, and deterrent controls to reduce the risk of physical theft? (Select TWO).
The following are the logs of a successful attack.
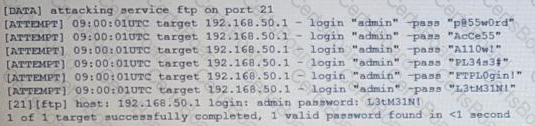
Which of the following controls would be BEST to use to prevent such a breach in the future?
A software company is analyzing a process that detects software vulnerabilities at the earliest stage possible. The goal is to scan the source looking for unsecure practices and weaknesses before the application is deployed in a runtime environment. Which of the following would BEST assist the company with this objective?
A company would like to provide flexibility for employees on device preference. However, the company is concerned about supporting too many different types of hardware. Which of the following deployment models will provide the needed flexibility with the GREATEST amount of control and security over company data and infrastructure?
Which of the following is the MOST secure but LEAST expensive data destruction method for data that is stored on hard drives?
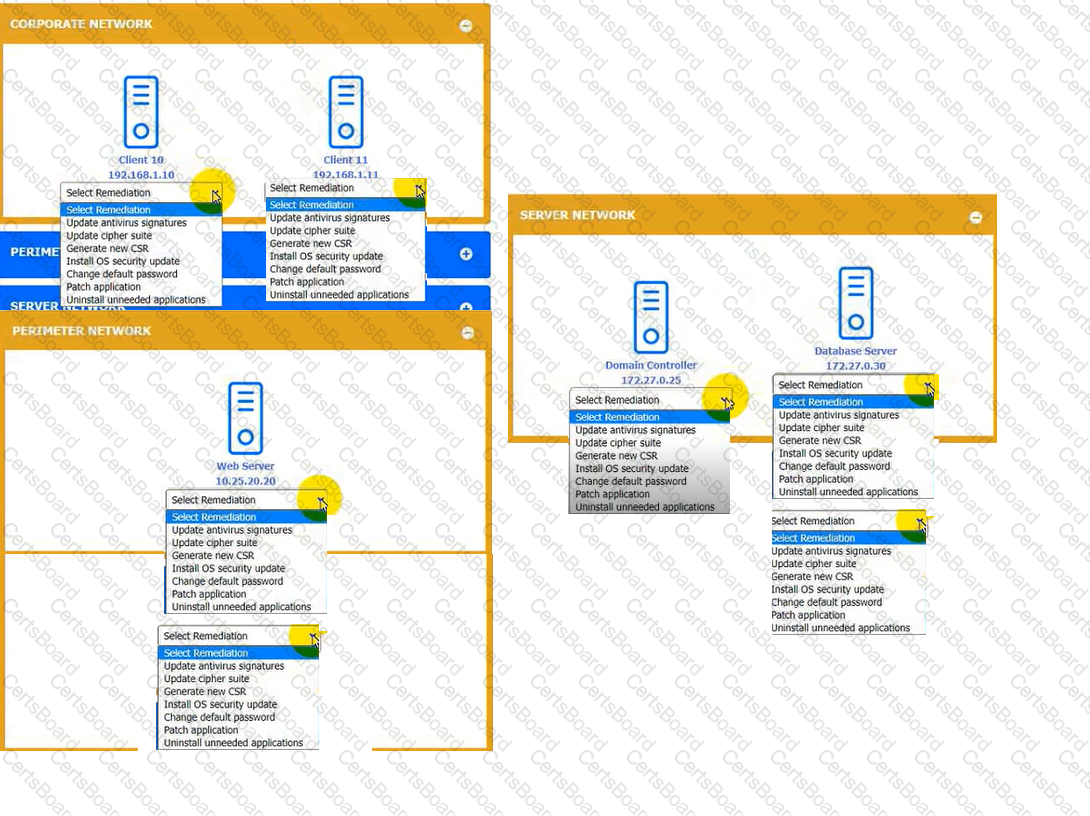
You received the output of a recent vulnerability assessment.
Review the assessment and scan output and determine the appropriate remedialion(s} 'or «ach dewce.
Remediation options may be selected multiple times, and some devices may require more than one remediation.
If at any time you would like to biing bade the initial state ot the simulation, please dick me Reset All button.
If a current private key is compromised, which of the following would ensure it cannot be used to decrypt ail historical data?
Which of the following provides a catalog of security and privacy controls related to the United States federal information systems?
An analyst is working on an email security incident in which the target opened an attachment containing a worm. The analyst wants to implement mitigation techniques to prevent further spread. Which of the following is the BEST course of action for the analyst to take?
A cybersecurity administrator needs to implement a Layer 7 security control on a network and block potential attacks. Which of the following can block an attack at Layer 7? (Select TWO).
During a forensic investigation, a security analyst discovered that the following command was run on a compromised host:
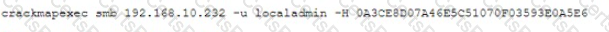
Which of the following attacks occurred?
A business is looking for a cloud service provider that offers a la carte services, including cloud backups, VM elasticity, and secure networking. Which of the following cloud service provider types should business engage?
A customer has reported that an organization's website displayed an image of a smiley (ace rather than the expected web page for a short time two days earlier. A security analyst reviews log tries and sees the following around the lime of the incident:
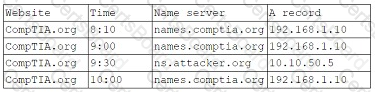
Which of the following is MOST likely occurring?
Which of the following would be best to ensure data is saved to a location on a server, is easily scaled, and is centrally monitored?
A Chief Information Security Officer (CISO) is evaluating the dangers involved in deploying a new ERP system for the company. The CISO categorizes the system, selects the controls that apply to the system, implements the controls, and then assesses the success of the controls before authorizing the system. Which of the following is the CISO using to evaluate the environment for this new ERP system?
While reviewing the /etc/shadow file, a security administrator notices files with the same values. Which of the following attacks should the administrator be concerned about?
Stakeholders at an organisation must be kept aware of any incidents and receive updates on status changes as they occur Which of the following Plans would fulfill this requirement?
A company would like to protect credit card information that is stored in a database from being exposed and reused. However, the current POS system does not support encryption. Which of the following would be BEST suited to secure this information?
(Give me related explanation and references from CompTIA Security+ SY0-601 documents for Correct answer option)
The management team has requested that the security team implement 802.1X into the existing wireless network setup. The following requirements must be met:
• Minimal interruption to the end user
• Mutual certificate validation
Which of the following authentication protocols would meet these requirements?