A consultant asks a customer to verify the ToR Switch data port configuration was done according to Nutanix best practices. The switch configuration must simplify future deployments and expansions.
Which two configuration actions will satisfy this requirement? (Choose two.)
How should a consultant verify that a Nutanix cluster can tolerate a single-node failure?
A consultant runs the Foundation Applet and discovers all the nodes. The consultant wants to use the latest version of Foundation for imaging for support purposes and to cover the latest hardware and software hypervisor support.
What should the consultant do to upgrade Foundation on a node?
A consultant is viewing an ESXi host via console without external network connectivity.
Which two IP addresses can be used to connect to the CVM (Choose two.)
A consultant is planning an installation and needs to collect configuration items to be used during the install. The data needed from the customer are IP addresses, Gateway, DNS servers, and NTP Servers.
Which Cluster Deployment document must be completed with the customer?
The following alert appears on the file server alerts tab in the file server dashboard:

Which two events can generate this alert? (choose two)
The following critical Availability Alert displays in prism Central:
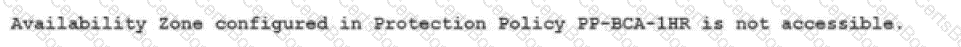
The protection Policy PP-BCA-1HR includes a business critical application with a 1-hour snapshot frequency.
What is causing this issue?
During Foundation, all nodes are imaged successfully. The cluster creation step fails. The consultant troubleshoots the issue and verifies that all Hosts and CVMs are up and running and responding to network pings.
Which method should the consultant select to create the cluster?
An administrator of a Nutanix Enterprise Cloud has microsegmentation enabled and a firewall VM installed. The security team notifies the administrator that one of the VMs hosted in the environment has been exhibiting suspect network activity. The administrator wants to isolate the VM from the production network, but must still be able to access it to perform diagnostics.
What should the administrator do to meet the requirement?
An administrator is deploying a three-tier application on a Nutanix Enterprise Cloud consisting of web, application, and database VMs. Traffic between the servers must be limited to specific services/ports. There is an application layer firewall VM deployed on one host in the cluster.
In which way should the administrator meet this requirement?


