You are deploying a new wireless solution with an Aruba Mobility Master (MM). Aruba Mobility Controllers (MCs), and campus APs (CAPs). The solution will include a WLAN that uses Tunnel for the forwarding mode and WPA3-Enterprise for the security option.
You have decided to assign the WLAN to VLAN 301, a new VLAN. A pair of core routing switches will act as the default router for wireless user traffic.
Which links need to carry VLAN 301?
You have been asked to rind logs related to port authentication on an ArubaOS-CX switch for events logged in the past several hours But. you are having trouble searching through the logs What is one approach that you can take to find the relevant logs?
What is a guideline for creating certificate signing requests (CSRs) and deploying server Certificates on ArubaOS Mobility Controllers (MCs)?
Two wireless clients, client 1 and client 2, are connected to an ArubaOS Mobility Controller. Subnet 10.1.10.10/24 is a network of servers on the other side of the ArubaOS firewall. The exhibit shows all three firewall rules that apply to these clients.
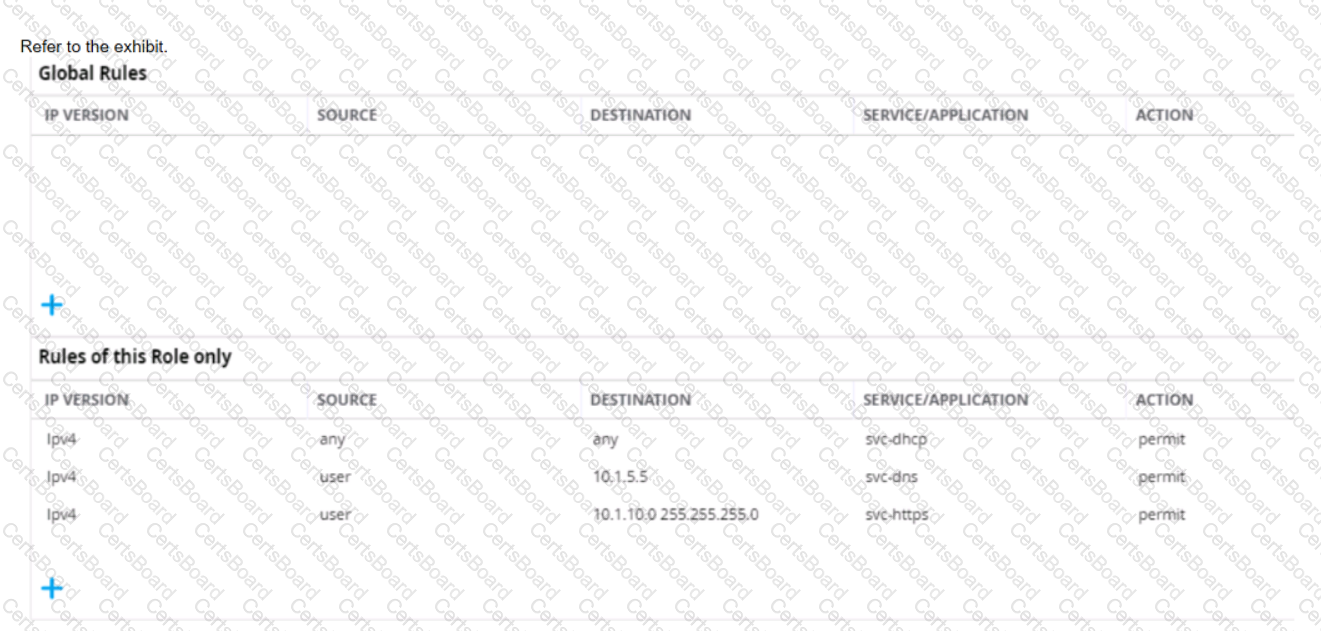
Which traffic is permitted?
You are troubleshooting an authentication issue for Aruba switches that enforce 802 IX10 a cluster of Aruba ClearPass Policy Manager (CPPMs) You know that CPPM Is receiving and processing the authentication requests because the Aruba switches are showing Access-Rejects in their statistics However, you cannot find the record tor the Access-Rejects in CPPM Access Tracker
What is something you can do to look for the records?
Refer to the exhibit, which shows the current network topology.
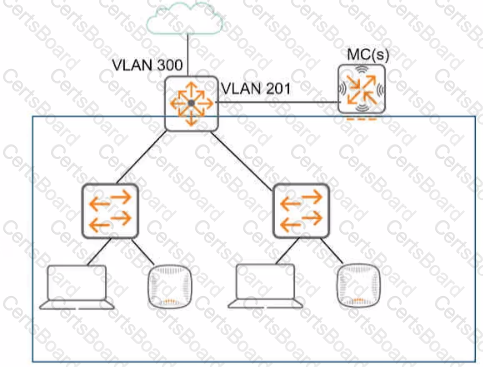
You are deploying a new wireless solution with an Aruba Mobility Master (MM). Aruba Mobility Controllers (MCs). and campus APs (CAPs). The solution will Include a WLAN that uses Tunnel for the forwarding mode and Implements WPA3-Enterprise security
What is a guideline for setting up the vlan for wireless devices connected to the WLAN?
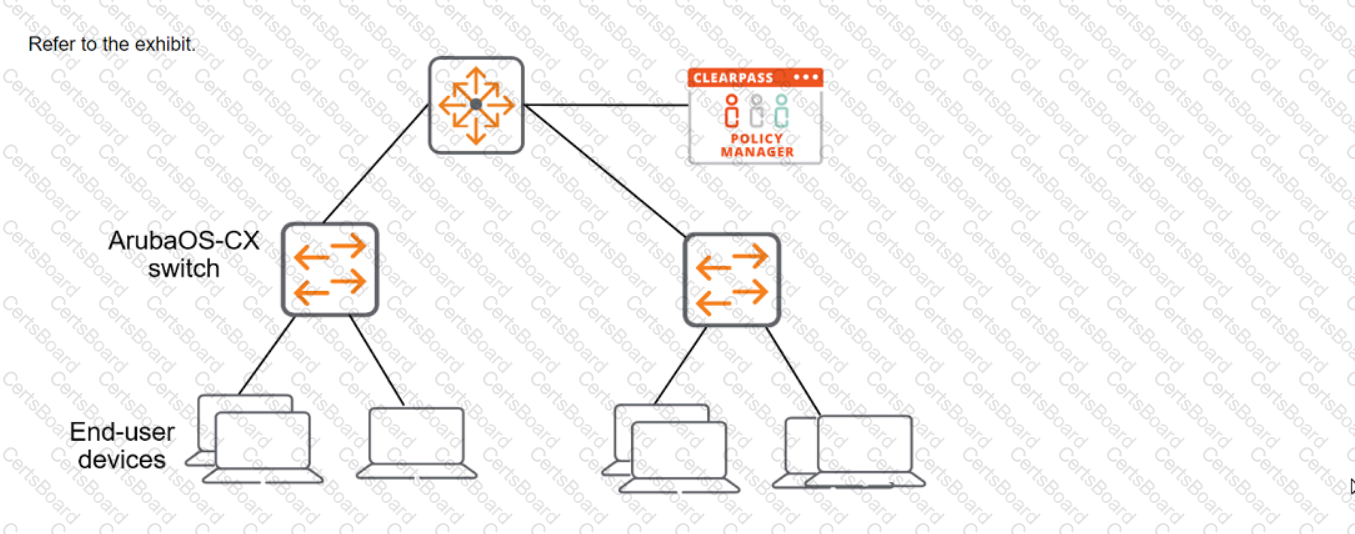
What is another setting that you must configure on the switch to meet these requirements?
What is one difference between EAP-Tunneled Layer security (EAP-TLS) and Protected EAP (PEAP)?


