How can hackers implement a man-in-the-middle (MITM) attack against a wireless client?
Your ArubaoS solution has detected a rogue AP with Wireless intrusion Prevention (WIP). Which information about the detected radio can best help you to locate the rogue device?
How does the ArubaOS firewall determine which rules to apply to a specific client's traffic?
You need to set up Aruba network infrastructure devices for management with SNMP. The SNMP server has this SNMPv3 user configured on it: username: airwave auth algorithm: sha auth key: fyluqp18@S!9a priv algorithm: aes priv key: 761oxaiaoeu19&
What correctly describes the setup on the infrastructure device?
What is a benefit of Protected Management Frames (PMF). sometimes called Management Frame Protection (MFP)?
Refer to the exhibit.
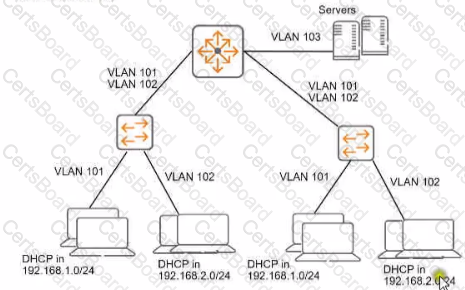
You need to ensure that only management stations in subnet 192.168.1.0/24 can access the ArubaOS-Switches' CLI. Web Ul. and REST interfaces The company also wants to let managers use these stations to access other parts of the network What should you do?
A company has Aruba Mobility Controllers (MCs). Aruba campus APs. and ArubaOS-CX switches. The company plans to use ClearPass Policy Manager (CPPM) to classify endpoints by type The ClearPass admins tell you that they want to run Network scans as part of the solution
What should you do to configure the infrastructure to support the scans?
Refer to the exhibit.
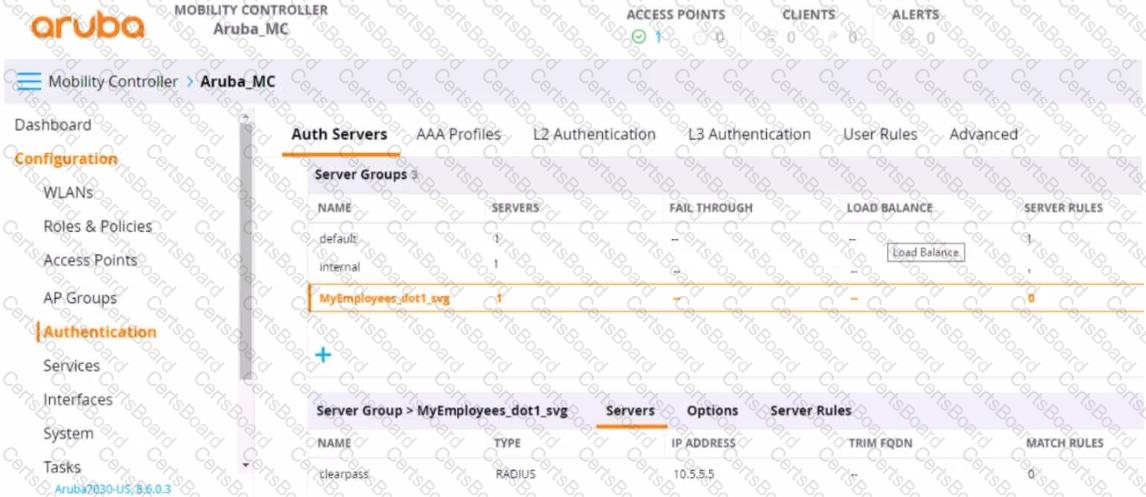
You have set up a RADIUS server on an ArubaOS Mobility Controller (MC) when you created a WLAN named "MyEmployees .You now want to enable the MC to accept change of authorization (CoA) messages from this server for wireless sessions on this WLAN.
What Is a part of the setup on the MC?
You have detected a Rogue AP using the Security Dashboard Which two actions should you take in responding to this event? (Select two)
A company has an ArubaOS solution. The company wants to prevent users assigned to the "user_group1" role from using gaming and peer-to-peer applications.
What is the recommended approach for these requirements?


