To prevent hackers from attacking user devices or networks through MA, C addresses, you can configure the MA, C addresses of untrusted users as black hole MA, C addresses to filter out illegal MA, C addresses.
R1 and R2 use directly connected interfaces to establish an EBGP peer relationship. R1 imports 2000:: 1/128 to BGR By default, which of the following is the next hop of the route from R2 to 2000:: 1/128?
EGP authentication can prevent illegal routers from establishing neighbors with B, CP routers. B, CP authentication can be divided into MD5
Authentication and Keychain authentication, which of the following BGP documents will carry the B, CGP Keychain authentication letter
interest? (header carry)
by executing___________The command can completely isolate the second and third layer users of different ports on the same LAN and cannot communicate. (Please use English and lowercase letters to complete the command, and the command cannot be abbreviated)
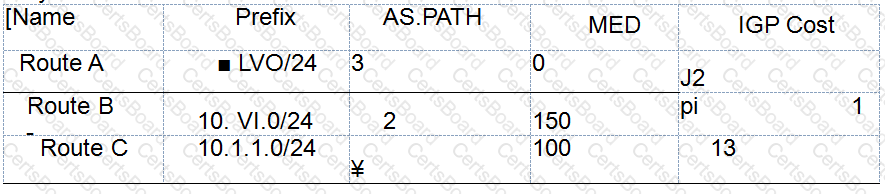
The routing attributes of the three routing entries are shown in the figure. Assuming that the next hops of the three routing entries are all reachable, when these three routing entries are
After the entries arrive at the BP router in order, by default, BGP will finally call a route
entry?
Regarding the MPLS forwarding process, the description of Ingress node forwarding is correct:
Regarding the BGPI MPLS IPVPN network architecture, which of the following descriptions is wrong?
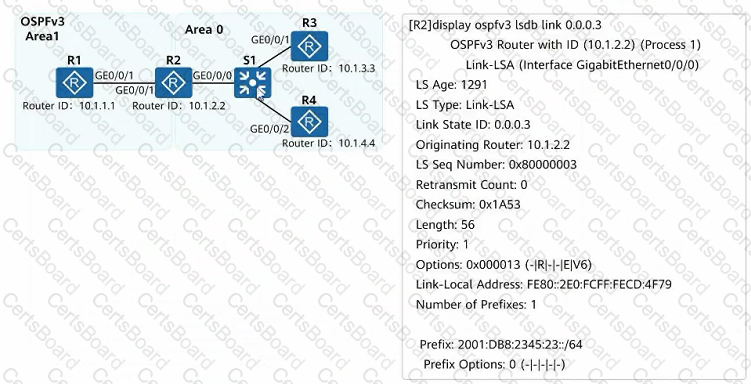
A campus has deployed IPv6 for service testing. There are 4 routers in the network, running 0SPFv3 to implement IPv6 network interconnection. As shown in the figure, an engineer checked the LSDB of R2 and intercepted one of the Link-LSAs. Which of the following statements is true about the description of this LSA?