Smith is an IT technician that has been appointed to his company's network vulnerability assessment team. He is the only IT employee on the team. The other team members include employees from Accounting,
Management, Shipping, and Marketing. Smith and the team members are having their first meeting to discuss how they will proceed. What is the first step they should do to create the network vulnerability assessment
plan?
As a network administrator, you have implemented WPA2 encryption in your corporate wireless network. The WPA2's_________integrity check mechanism provides security against a replay attack
Which of the following defines the extent to which an interruption affects normal business operations and the amount of revenue lost due to that interruption?
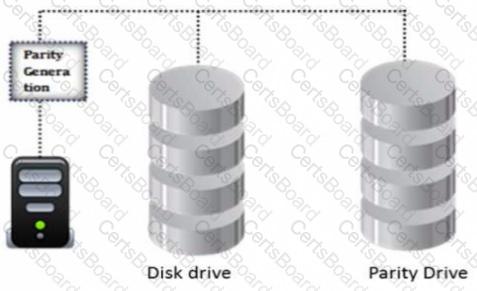
Identify the minimum number of drives required to setup RAID level 5.