Which of the Windows security component is responsible for controlling access of a user to Windows resources?
John has planned to update all Linux workstations in his network. The organization is using various Linux distributions including Red hat, Fedora and Debian. Which of following commands will he use to
update each respective Linux distribution?
XX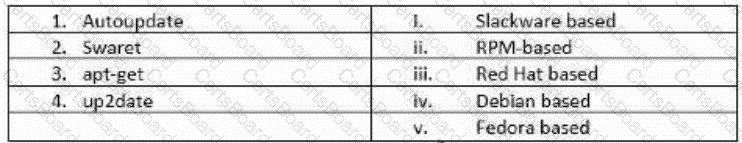
What should a network administrator perform to execute/test the untrusted or untested programs or code from untrusted or unverified third-parties without risking the host system or OS?
A local bank wants to protect their cardholder data. Which standard should the bark comply with in order to ensure security of this data?


