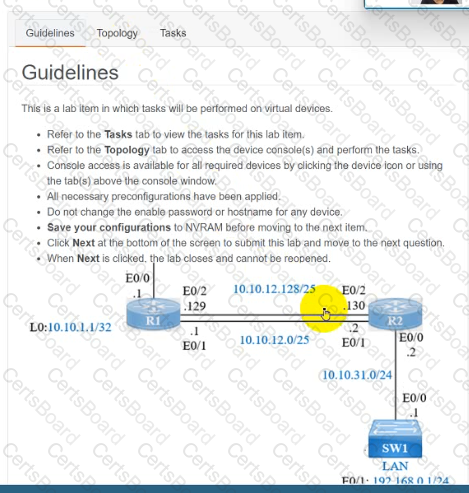

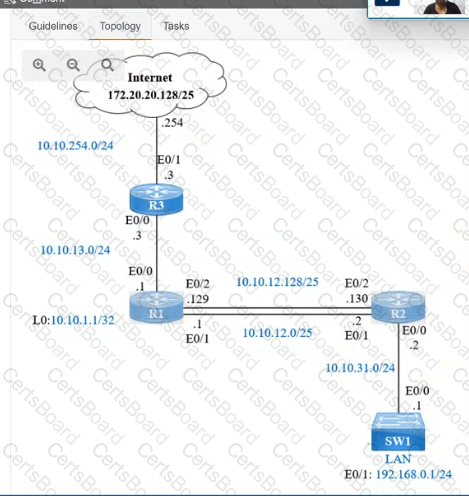
IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1:
1. Configure reachability to the switch SW1 LAN subnet in router R2.
2. Configure default reachability to the Internet subnet in router R1.
3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2.
4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1. and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.
What is the difference between controller-based networks and traditional networks as they relate to control-plane and/or data-plane functions?
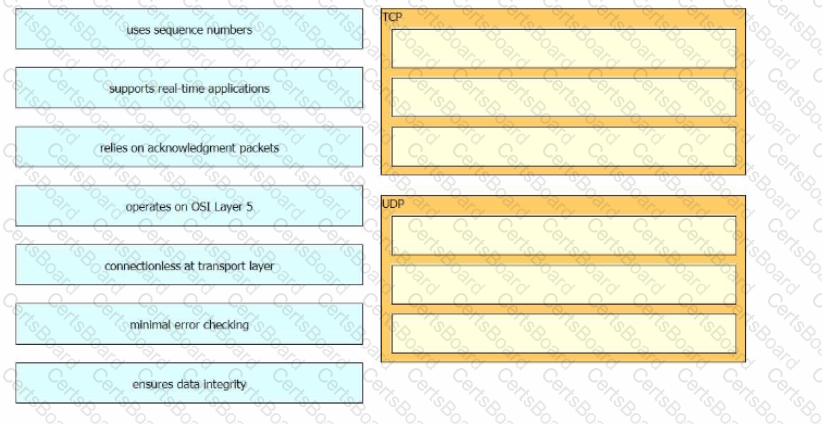
Drag and drop the TCP and UDP characteristics from the left onto the supporting protocols on the right. Not all options are used.
Which WLC management connection type is vulnerable to man-in-the-middIe attacks?
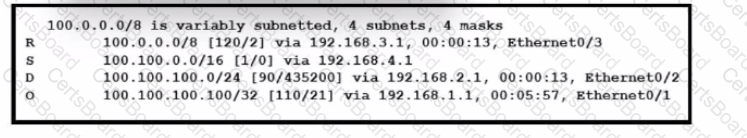
Refer to the exhibit. How will the device handle a packet destined to IP address 100.100.100.100?
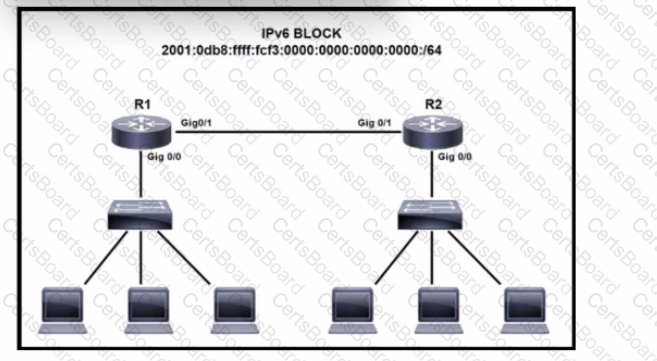
Refer to the exhibit. IPv6 is being Implemented within the enterprise. The command Ipv6 unlcast-routing is configure. Interlace GlgO/0 on R1 must be configured to provide a dynamic assignment using the assigned IPv6 block Which command accomplishes this task?
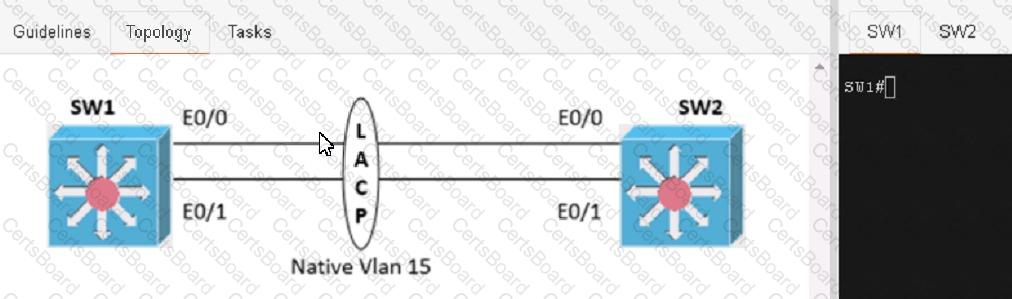
Physical connectivity is implemented between the two Layer 2 switches, and the network connectivity between them must be configured
1. Configure an LACP EtherChannel and number it as 1; configure it between switches SW1 and SVV2 using interfaces Ethernet0/0 and Ethernet0/1 on both sides. The LACP mode must match on both ends
2 Configure the EtherChannel as a trunk link.
3. Configure the trunk link with 802.1 q tags.
4. Configure the native VLAN of the EtherChannel as VLAN 15.
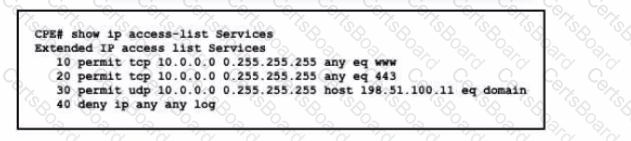
Refer to the exhibit. This ACL is configured to allow client access only to HTTP, HTTPS, and DNS services via UDP. The new administrator wants to add TCP access to the DNS service. Which configuration updates the ACL efficiently?
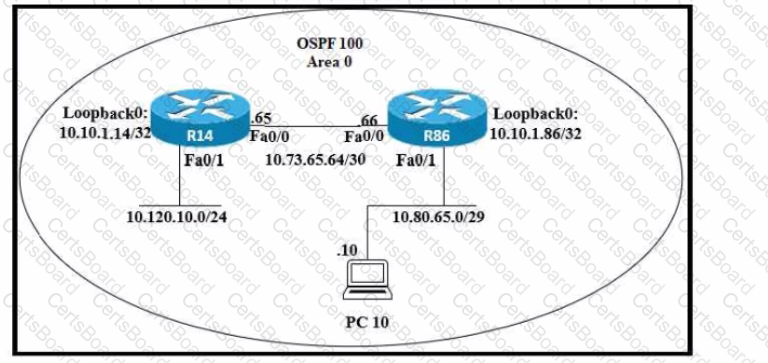
Refer to the exhibit. An engineer just installed network 10.120.10.0/24. Which configuration must be applied to the R14 router to add the new network to its OSPF routing table?
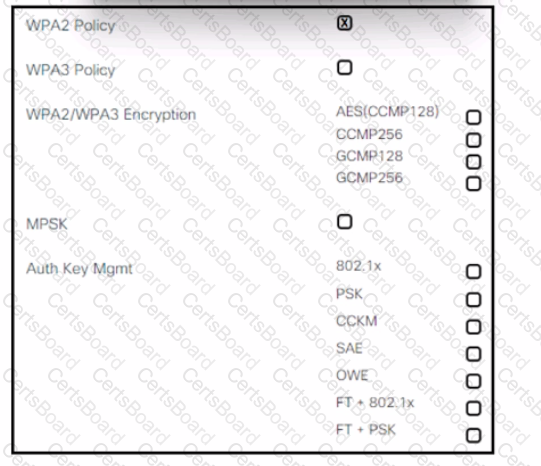
Refer to the exhibit. An engineer is creating a secure preshared key based SSID using WPA2 for a wireless network running on 2.4 GHz and 5 GHz. Which two tasks must the engineer perform to complete the process? (Choose two.)
Why is UDP more suitable than TCP tor applications that require low latency, such as VoIP?
Refer to the exhibit. The user has connectivity to devices on network 192.168.3 0/24 but cannot reach users on the network 10.10.1.0724.
What is the first step to verify connectivity?

A network administrator wants the syslog server to filter incoming messages into different files based on their Importance. Which filtering criteria must be used?
What are two facts that differentiate optical-fiber cabling from copper cabling? (Choose two.)
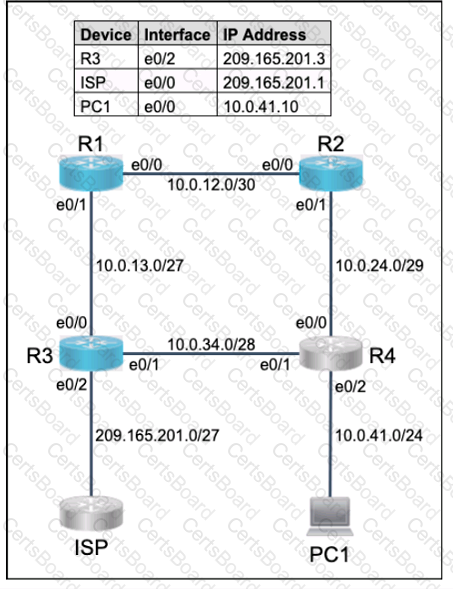
All physical cabling is in place. Router R4 and PCI are fully configured and
inaccessible. R4's WAN interfaces use .4 in the last octet for each subnet.
Configurations should ensure that connectivity is established end-to-end.
1 . Configure static routing to ensure RI prefers the path through R2 to
reach only PCI on R4's LAN
2. Configure static routing that ensures traffic sourced from RI will take
an alternate path through R3 to PCI in the event of an outage along
the primary path
3. Configure default routes on RI and R3 to the Internet using the least number of hops
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
What is the main difference between traditional networks and controller-based networking?
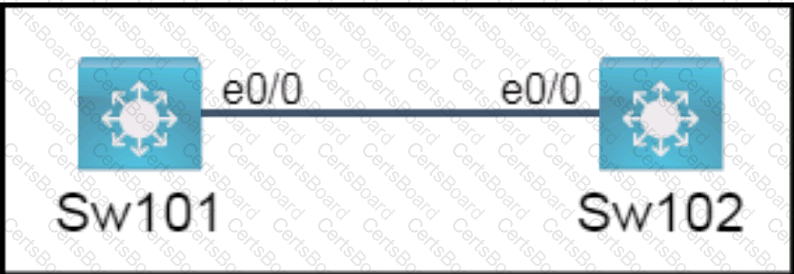
All physical cabling is in place. A company plans to deploy 32 new sites.
The sites will utilize both IPv4 and IPv6 networks.
1 . Subnet 172.25.0.0/16 to meet the subnet requirements and maximize
the number of hosts
Using the second subnet
• Assign the first usable IP address to e0/0 on Sw1O1
• Assign the last usable IP address to e0/0 on Sw102
2. Subnet to meet the subnet requirements and maximize
the number of hosts
c Using the second subnet
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on e0/0 on Sw101
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on eO/O on swi02
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
How does machine learning improve the detection of unauthorized network access?
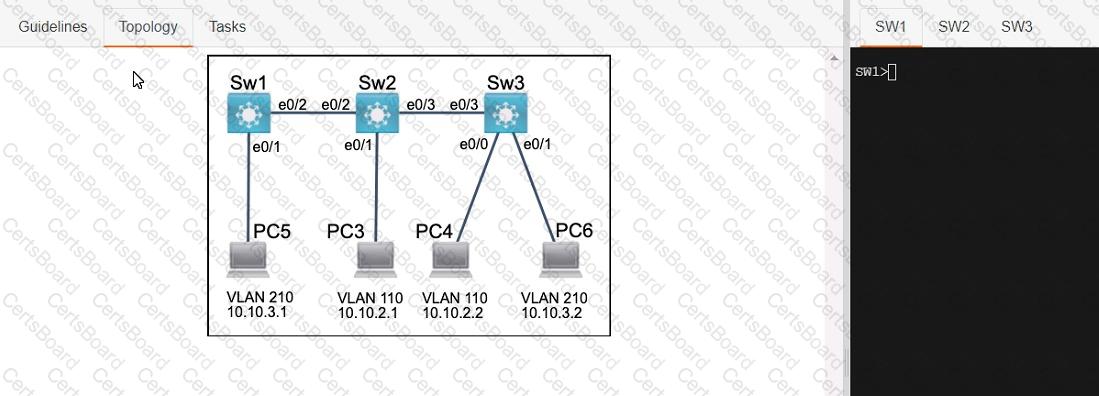
Three switches must be configured for Layer 2 connectivity. The company requires only the designated VLANs to be configured on their respective switches and permitted accross any links between switches for security purposes. Do not modify or delete VTP configurations.
The network needs two user-defined VLANs configured:
VLAN 110: MARKETING
VLAN 210: FINANCE
1. Configure the VLANs on the designated switches and assign them as access ports to the interfaces connected to the PCs.
2. Configure the e0/2 interfaces on Sw1 and Sw2 as 802.1q trunks with only the required VLANs permitted.
3. Configure the e0/3 interfaces on Sw2 and Sw3 as 802.1q trunks with only the required VLANs permitted.