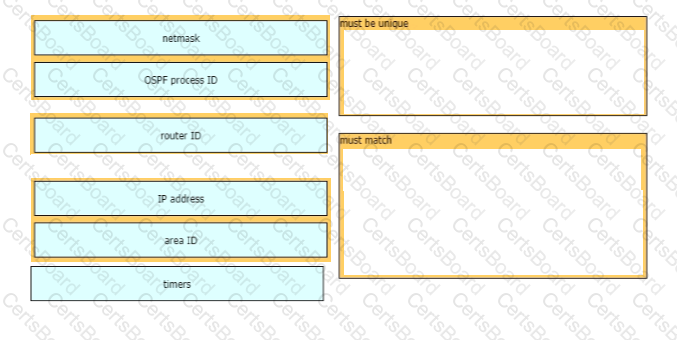
A network engineer is configuring an OSPFv2 neighbor adjacency Drag and drop the parameters from the left onto their required categories on the right. Not all parameters are used
When configuring a WLAN with WPA2 PSK in the Cisco Wireless LAN Controller GUI, which two formats are available to select? (Choose two)
When a site-to-site VPN is configured, which IPsec mode provides encapsulation and encryption of the entire original P packet?
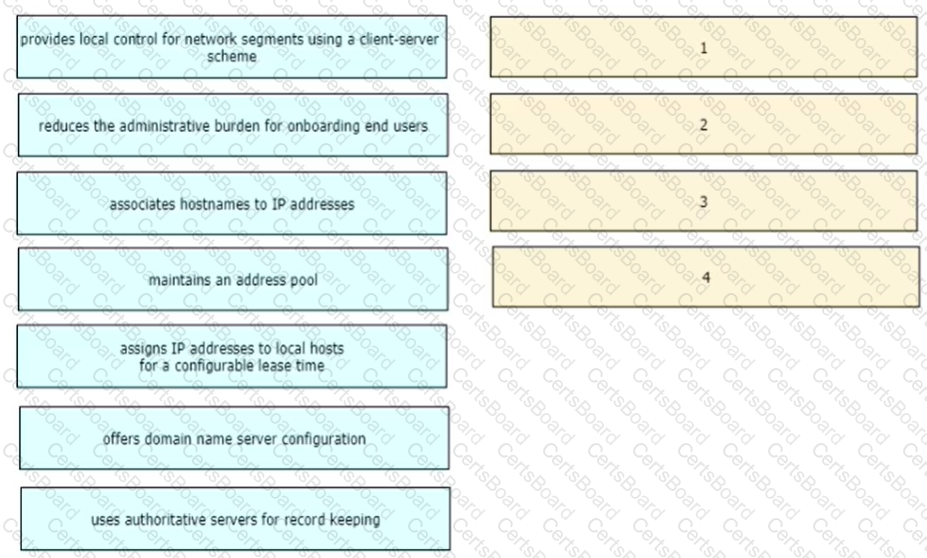
Drag and drop the functions of DHCP from the left onto any of the positions on the right Not all functions are used
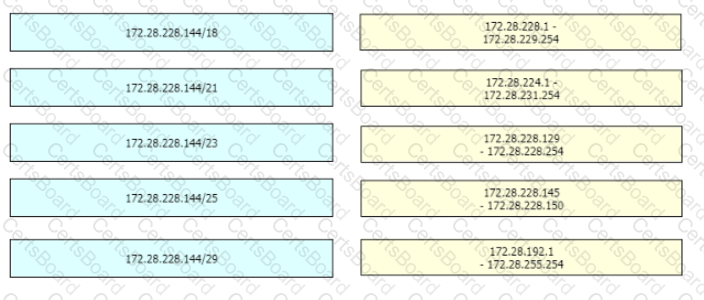
Drag and drop the IPv4 network subnets from the left onto the correct usable host ranges on the right
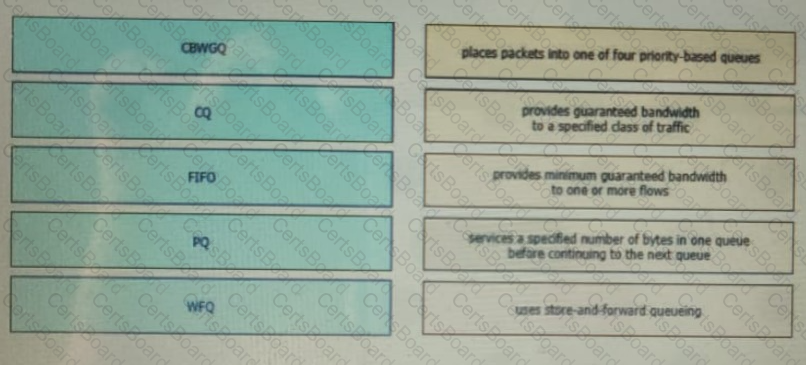
Drag and drop the QoS congestion management terms from the left onto the description on the right.
When using Rapid PVST+, which command guarantees the switch is always the root bridge for VLAN 200?
Refer to the exhibit.
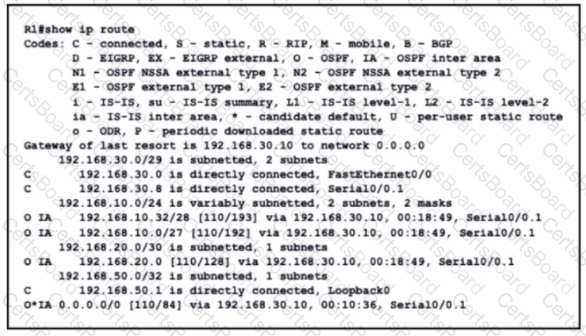
What is the metric of the route to the 192.168.10.33/28 subnet?
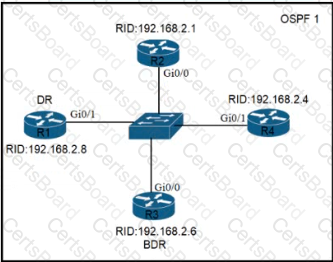
Refer to the exhibit. All routers in the network are configured R2 must be the DR. After the engineer connected the devices, R1 was elected as the DR. Which command sequence must be configure on R2 to Be elected as the DR in the network?

Refer to the exhibit.

The network administrator wants VLAN 67 traffic to be untagged between Switch 1 and Switch 2 while all other VLANs are to remain tagged.
Which command accomplishes this task?
A network engineer must back up 20 network router configurations globally within a customer environment. Which protocol allows the engineer to perform this function using the Cisco IOS MIB?
Which mode must be used to configure EtherChannel between two switches without using a negotiation protocol?
Which function is performed by the collapsed core layer in a two-tier architecture?
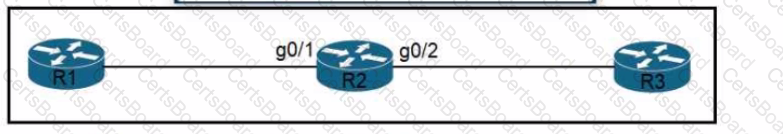
Refer to the exhibit Routers R1 R2 and R3 use a protocol to identify their neighbors' IP addresses hardware platforms, and software versions. A network engineer must configure R2 to avoid sharing any neighbor information with R3, and maintain its relationship with R1. What action meets this requirement?
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.

Which alternative to password authentication Is Implemented to allow enterprise devices to log in to the corporate network?


