Which security program element involves installing badge readers on data-center doors to allow workers to enter and exit based on their job roles?
Which feature on the Cisco Wireless LAN Controller when enabled restricts management access from specific networks?
What are two improvements provided by automation for network management in an SDN environment? (Choose two)
Which spanning-tree enhancement avoids the learning and listening states and immediately places ports in the forwarding state?
Refer to the exhibit.

Site A was recently connected to site B over a new single-mode fiber path. Users at site A report Intermittent connectivity Issues with applications hosted at site B. What is the reason for the problem?
Which technology must be implemented to configure network device monitoring with the highest security?
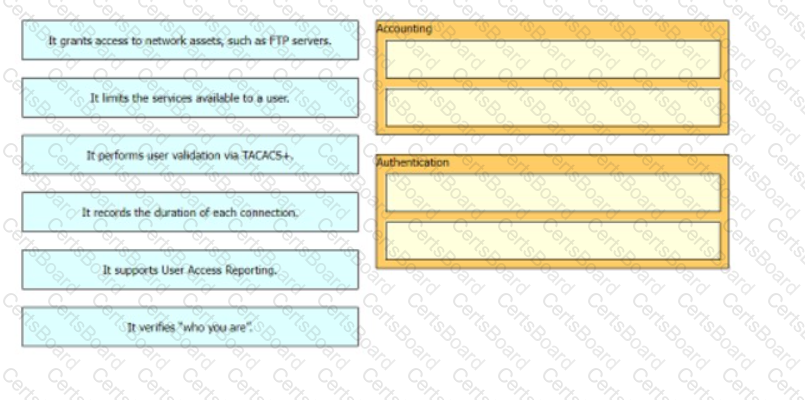
Drag and drop the statements about AAA services firm the left onto the corresponding AAA services on the right Not all options are used.
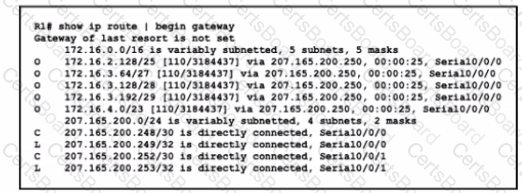
Refer to the exhibit.
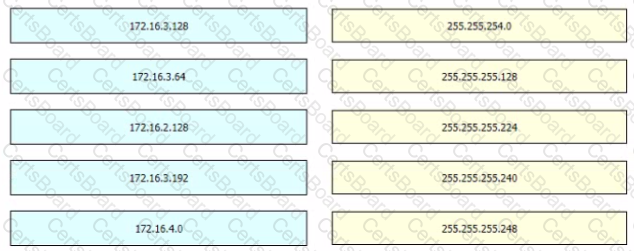
Drag and drop the learned prefixes from the left onto the subnet masks on the right
Refer to the exhibit.
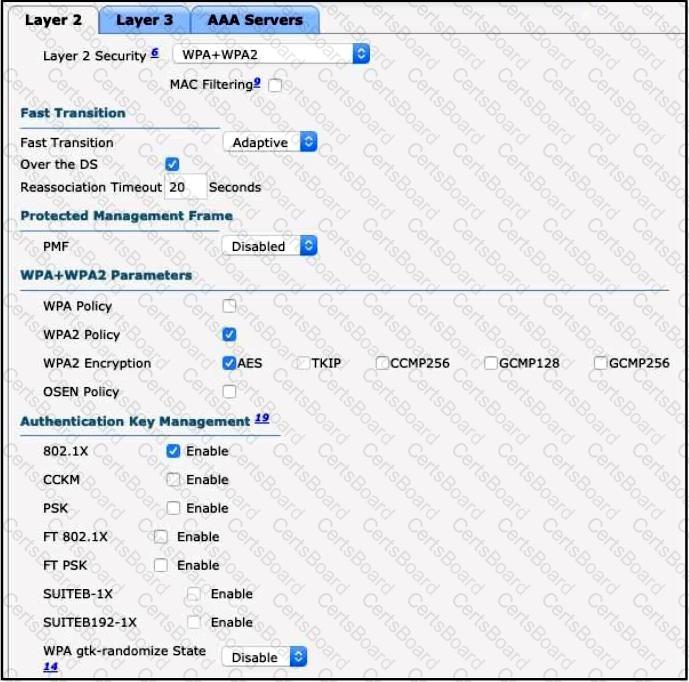
Clients on the WLAN are required to use 802.11r. What action must be taken to meet the requirement?
A network engineer must migrate a router loopback interface to the IPv6 address space. If the current IPv4 address of the interface is 10.54.73.1/32, and the engineer configures IPv6 address 0.0.0.0.0:ffff:a36:4901, which prefix length must be used?
Refer to the exhibit.
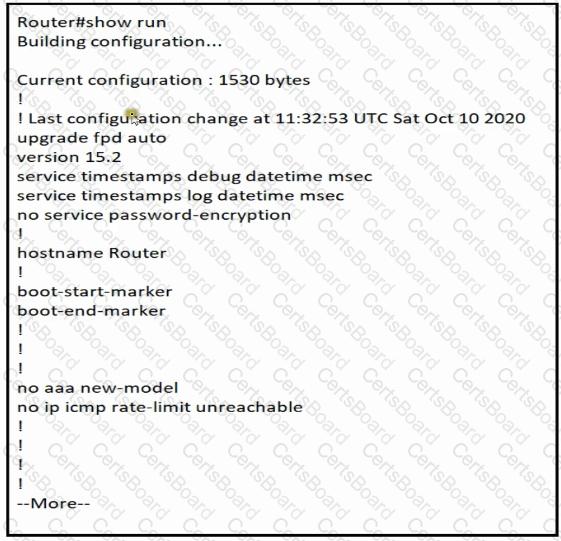
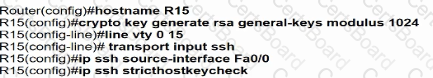
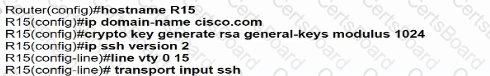
Which minimum configuration items are needed to enable Secure Shell version 2 access to R15?
A)
B)
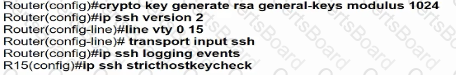
C)

D)
Refer to the exhibit.

Which action must be taken so that neighbofing devices rapidly discover switch Cat9300?
Refer to the exhibit.

How many objects, Keys and JSON list values are present?
Drag and drop the functions of AAA supporting protocols from the left onto the protocols on the right.

Which action implements physical access control as part of the security program of an organization?


