What are two characteristics of the distribution layer in a three-tier network architecture? (Choose two.)
Refer to the exhibit.
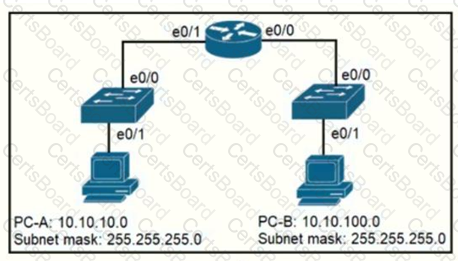
When PC-A sends traffic to PC-B, which network component is in charge of receiving the packet from PC-A verifying the IP addresses, and forwarding the packet to PC-B?
In which two ways does a password manager reduce the chance of a hacker stealing a users password? (Choose two.)
Refer to the exhibit.
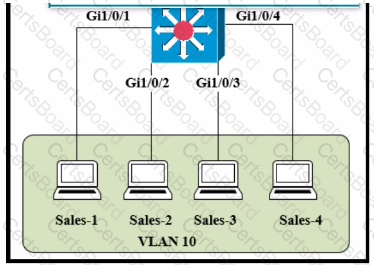
The entire contents of the MAC address table are shown. Sales-4 sends a data frame to Sales-1.
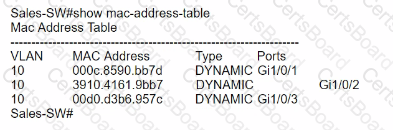
What does the switch do as it receives the frame from Sales-4?
Which implementation provides the strongest encryption combination for the wireless environment?
A HCP pool has been created with the name CONTROL. The pool uses the next to last usable IP address as the default gateway for the DHCP clients. The server is located at 172.16 32.15. What is the step in the process for clients on the 192.168.52.0/24 subnet to reach the DHCP server?
Which solution is appropriate when mitigating password attacks where the attacker was able to sniff the clear-text password of the system administrator?
Which configuration management mechanism uses TCP port 22 by default when communicating with managed nodes?
Refer to the exhibit.
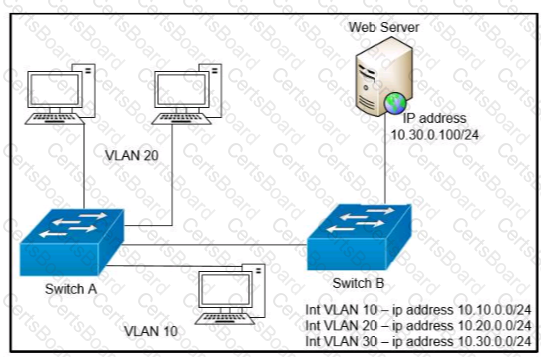
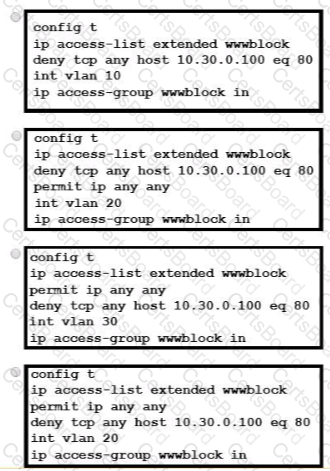
A network engineer must block access for all computers on VLAN 20 to the web server via HTTP All other computers must be able to access the web server Which configuration when applied to switch A accomplishes this task?
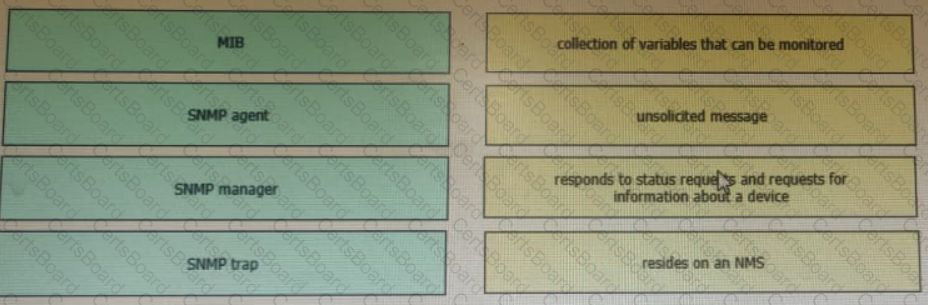
Drag and drop the SNMP components from the left onto the descriptions on the right.
Refer to the exhibit.
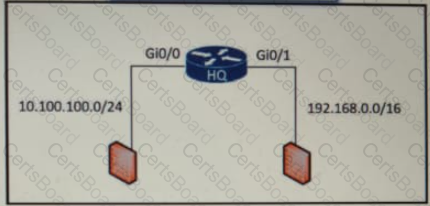
An access list is required to permit traffic from any host on interface G0/0 and deny traffic from interface G/0/1. Which access list must be applied?

What are two benefits of controller-based networking compared to traditional networking?


