How do AAA operations compare regarding user identification, user services and access control?
Which goal is achieved by the implementation of private IPv4 addressing on a network?
On workstations running Microsoft Windows, which protocol provides the default gateway for the device?
What provides centralized control of authentication and roaming In an enterprise network?
Refer to the exhibit.
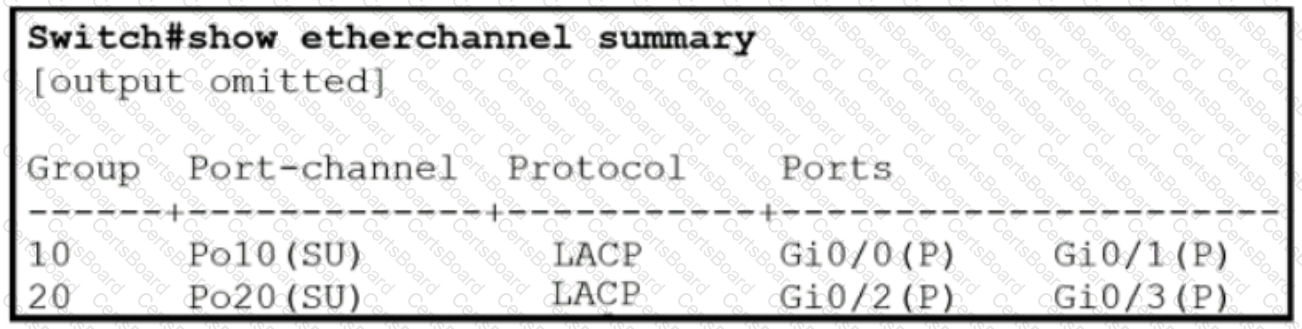
Which two commands were used to create port channel 10? (Choose two )

What makes Cisco DNA Center different from traditional network management applications and their management of networks?
Refer to the exhibit.
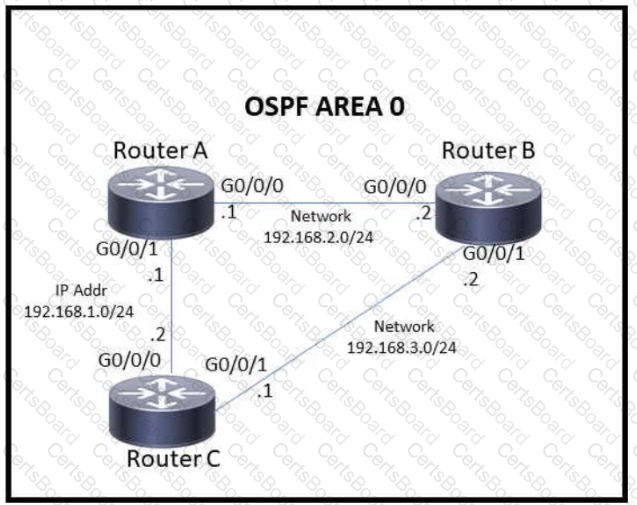
Which action must be taken to ensure that router A is elected as the DR for OSPF area 0?
Refer to the exhibit.
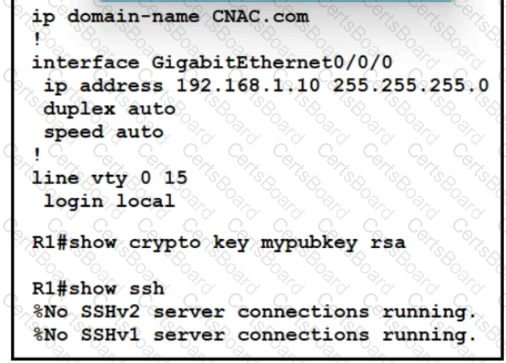
Which two commands must be added to update the configuration of router R1 so that it accepts only encrypted connections? (Choose two )
Which action does the router take as it forwards a packet through the network?
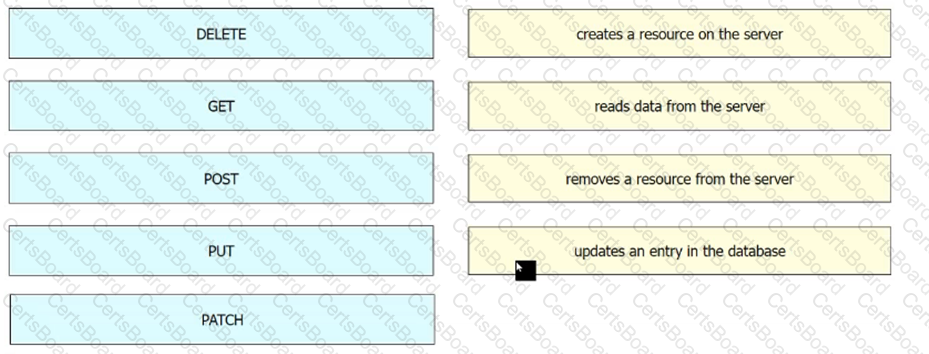
Drag and drop the REST API call method for HTTP from the left onto the action they perform on the right.
Refer to the exhibit.
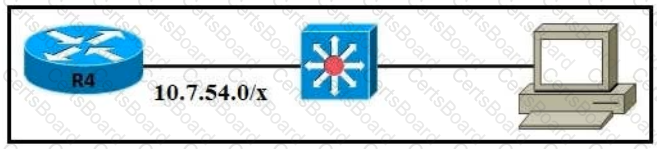
The router has been configured with a supernet to accommodate the requirement for 380 users on a subnet The requirement already considers 30% future growth. Which configuration verifies the IP subnet on router R4?
A)
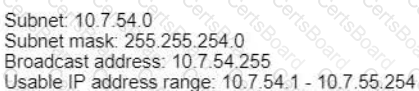
B)
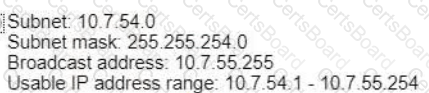
C)
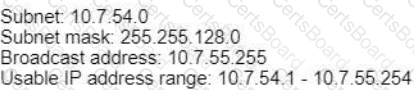
D)
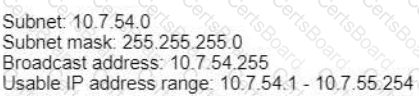
An engineer must configure an OSPF neighbor relationship between router R1 and R3 The authentication configuration has been configured and the connecting interfaces are in the same 192.168 1.0/30 sublet. What are the next two steps to complete the configuration? (Choose two.)
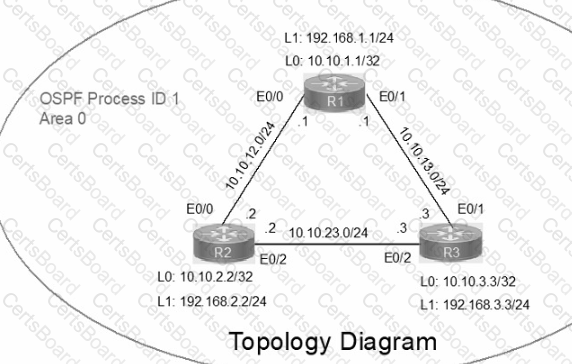
IP connectivity between the three routers is configured. OSPF adjacencies must be established.
1. Configure R1 and R2 Router IDs using the interface IP addresses from the link that is shared between them.
2. Configure the R2 links with a max value facing R1 and R3. R2 must become the DR. R1 and R3 links facing R2 must remain with the default OSPF configuration for DR election. Verify the configuration after clearing the OSPF process.
3. Using a host wildcard mask, configure all three routers to advertise their respective Loopback1 networks.
4. Configure the link between R1 and R3 to disable their ability to add other OSPF routers.
Which action is taken by a switch port enabled for PoE power classification override?

Refer to the exhibit. Which interface does a packet take to reach the destination address of 10.10.10.147?
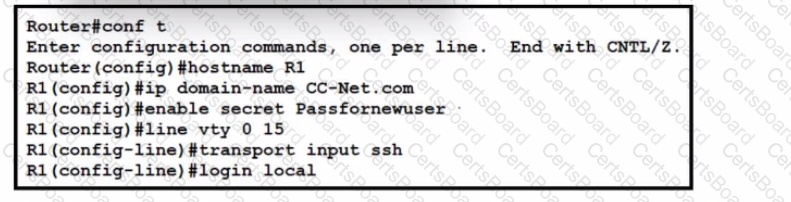
Refer to the exhibit. A network administrator is configuring a router for user access via SSH. The service-password encryption command has been issued. The configuration must meet these requirements:
• Create the username as CCUser.
• Create the password as NA!2Scc.
• Encrypt the user password.
What must be configured to meet the requirements?
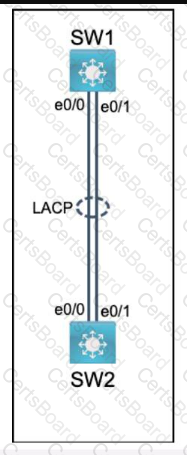
Physical connectivity is implemented between the two Layer 2 switches,
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
==================
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.