Drag and drop the statements about networking from the left onto the corresponding networking types on the right

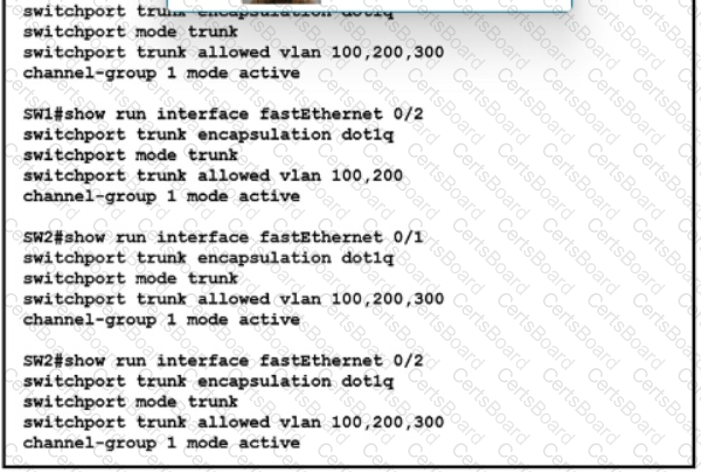
Refer to the exhibit. An engineer is building a new Layer 2 LACP EtherChannel between SW1 and SW2. and they executed the given show commands to verify the work Which additional task must be performed so that the switches successfully bundle the second member in the LACP port-channel?
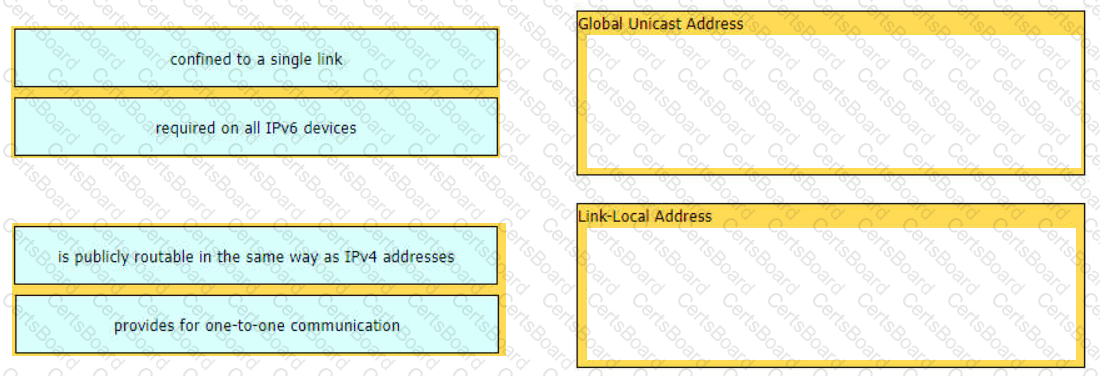
Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Refer to the exhibit.
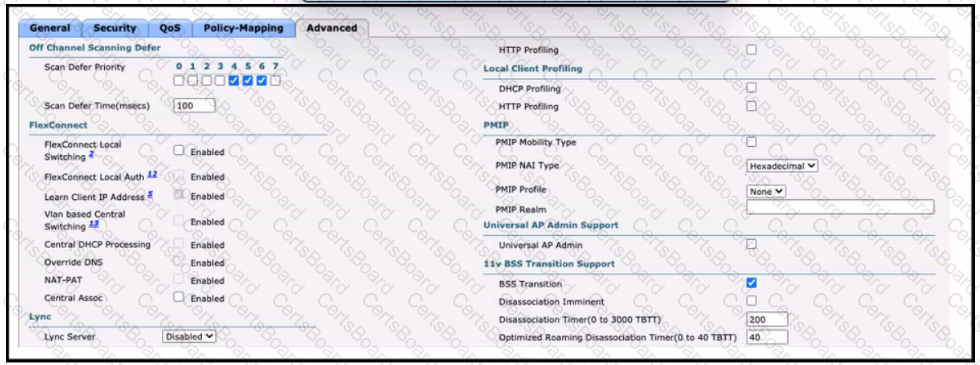
An architect is managing a wireless network with APs from several branch offices connecting to the WLC in the data center. There is a new requirement for a single WLAN to process the client data traffic without sending it to the WLC. Which action must be taken to complete the request?
A network architect is deciding whether to implement Cisco autonomous access points or lightweight access points. Which fact about firmware updates must the architect consider? Unlike lightweight access points, which require
A client experiences slow throughput from a server that is directly connected to the core switch in a data center. A network engineer finds minimal latency on connections to the server, but data transfers are unreliable, and the output of the show Interfaces counters errors command shows a high FCS-Err count on the interface that is connected to the server. What is the cause of the throughput issue?
Refer to the exhibit.
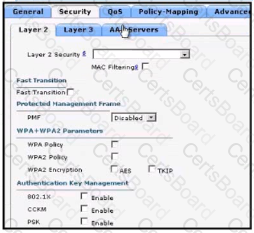
What are the two steps an engineer must take to provide the highest encryption and authentication using domain credentials from LDAP?
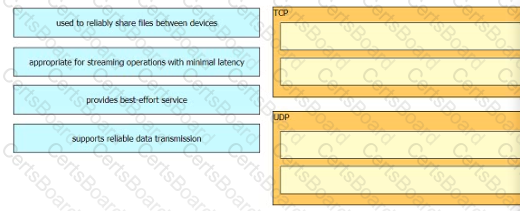
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
What is the advantage of separating the control plane from the data plane within an SDN network?
Refer to the exhibit.
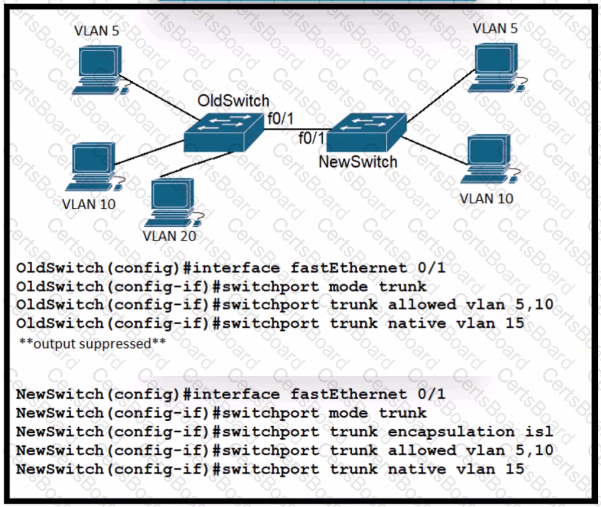
A new VLAN and switch are added to the network. A remote engineer configures OldSwitch and must ensure that the configuration meets these requirements:
• accommodates current configured VLANs
• expands the range to include VLAN 20
• allows for IEEE standard support for virtual LANs
Which configuration on the NewSwitch side of the link meets these requirements?
A)

B)
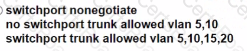
C)
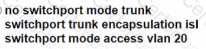
D)

What determines the sequence in which materials are planned during the material requirements planning (MRP) run?
Refer to the exhibit.
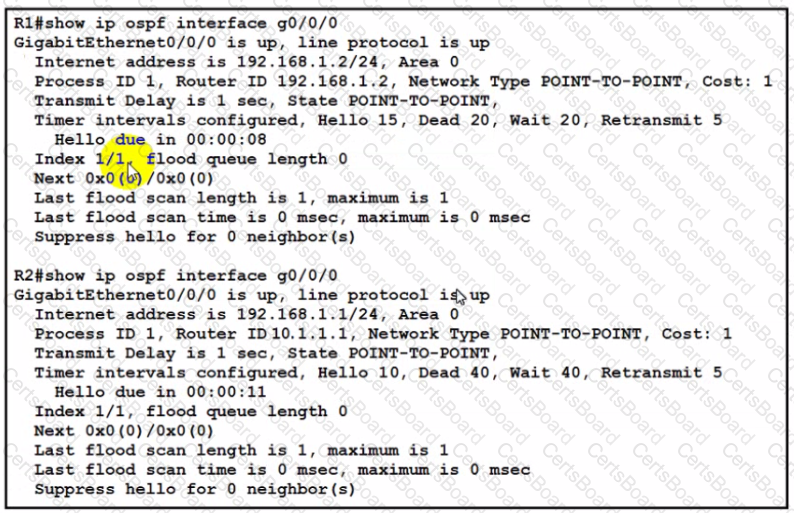
The network engineer is configuring router R2 as a replacement router on the network After the initial configuration is applied it is determined that R2 failed to show R1 as a neighbor Which configuration must be applied to R2 to complete the OSPF configuration and enable it to establish the neighbor relationship with R1?
A)
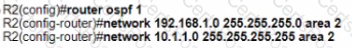
B)

C)

D)



