Which of the following ensures an organization can continue to do business with minimal interruption in the event of a major disaster?
An organization hired a third party to test its internal server environment for any exploitable vulnerabilities and to gain privileged access. The tester compromised several servers, and the organization was unable to detect any of the compromises. Which of the following actions would be best for the company to take to address these findings?
A systems administrator at a healthcare organization is setting up a server to securely store patient data. Which of the following must be ensured when storing PHI?
A newly implemented wireless network is designed so that visitors can connect to the wireless network for business activities. The legal department is concerned that visitors might connect to the network and perform illicit activities. Which of the following should the security team implement to address this concern?
Which of the following best practices gives administrators a set period to perform changes to an operational system to ensure availability and minimize business impacts?
After an audit, an administrator discovers all users have access to confidential data on a file server. Which of the following should the administrator use to restrict access to the data quickly?
Which of the following ensures an organization can continue to do business with minimal interruption in the event of a major disaster?
Law enforcement officials sent a company a notification that states electronically stored information and paper documents cannot be destroyed. Which of the following explains this process?
A manufacturing company has several one-off legacy information systems that cannot be migrated to a newer OS due to software compatibility issues. The OSs are still supported by the vendor but the industrial software is no longer supported The Chief Information Security Officer has created a resiliency plan for these systems that will allow OS patches to be installed in a non-production environment, white also creating backups of the systems for recovery. Which of the following resiliency techniques will provide these capabilities?
During a security incident the security operations team identified sustained network traffic from a malicious IP address: 10.1.4.9 A security analyst is creating an inbound firewall rule to block the IP address from accessing the organization's network. Which of the following fulfills this request?
A security analyst is investigating what appears to be unauthorized access to a corporate web application. The security analyst reviews the web server logs and finds the following entries:
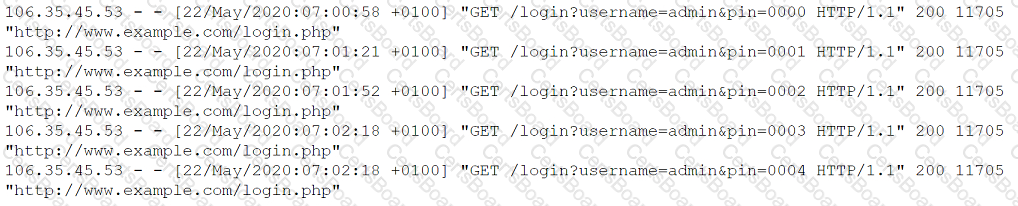
Which of the following password attacks is taking place?
To reduce and limit software and infrastructure costs the Chief Information Officer has requested to move email services to the cloud. The cloud provider and the organization must have secunty controls to protect sensitive data Which of the following cloud services would best accommodate the request?
During an assessment, a systems administrator found several hosts running FTP and decided to immediately block FTP communications at the firewall. Which of the following describes the
greatest risk associated with using FTP?
A company needs to centralize its logs to create a baseline and have visibility on its security events Which of the following technologies will accomplish this objective?
A company is auditing the manner in which its European customers’ personal information is handled. Which of the following should the company consult?
A security administrator needs to inspect in-transit files on the enterprise network to search for PI I credit card data, and classification words Which of the following would be the best to use?
Which of the following roles is responsible for defining the protection type and Classification type for a given set of files?
An organization with a low tolerance for user inconvenience wants to protect laptop hard drives against loss or data theft. Which of the following would be the most acceptable?
Two organizations are discussing a possible merger Both Organizations Chief Fi-nancial Officers would like to safely share payroll data with each Other to de-termine if the pay scales for different roles are similar at both organizations Which Of the following techniques would be best to protect employee data while allowing the companies to successfully share this information?