Which of the following is the BEST resource for obtaining payloads against specific network infrastructure products?
ion tester is attempting to get more people from a target company to download and run an executable. Which of the following would be the.. :tive way for the tester to achieve this objective?
A penetration tester needs to perform a vulnerability scan against a web server. Which of the following tools is the tester MOST likely to choose?
A penetration tester utilized Nmap to scan host 64.13.134.52 and received the following results:
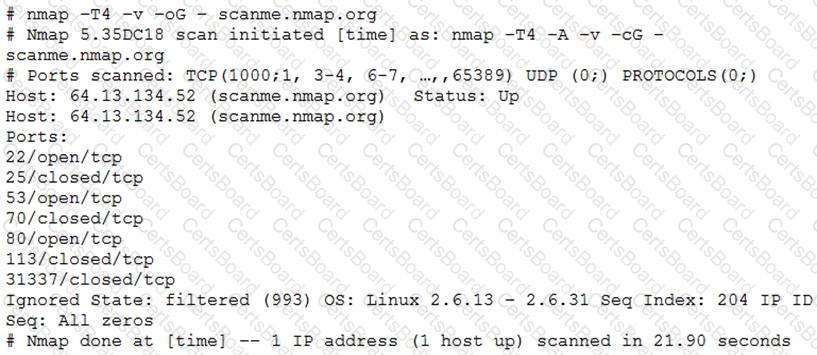
Based on the output, which of the following services are MOST likely to be exploited? (Choose two.)
Which of the following provides an exploitation suite with payload modules that cover the broadest range of target system types?
A penetration tester opened a reverse shell on a Linux web server and successfully escalated privileges to root. During the engagement, the tester noticed that another user logged in frequently as root to perform work tasks. To avoid disrupting this user’s work, which of the following is the BEST option for the penetration tester to maintain root-level persistence on this server during the test?
The provision that defines the level of responsibility between the penetration tester and the client for preventing unauthorized disclosure is found in the:
A penetration tester found several critical SQL injection vulnerabilities during an assessment of a client's system. The tester would like to suggest mitigation to the client as soon as possible.
Which of the following remediation techniques would be the BEST to recommend? (Choose two.)
A client evaluating a penetration testing company requests examples of its work. Which of the following represents the BEST course of action for the penetration testers?
During a web application test, a penetration tester was able to navigate to https://company.com and view all links on the web page. After manually reviewing the pages, the tester used a web scanner to automate the search for vulnerabilities. When returning to the web application, the following message appeared in the browser: unauthorized to view this page. Which of the following BEST explains what occurred?


