A company hired a penetration-testing team to review the cyber-physical systems in a manufacturing plant. The team immediately discovered the supervisory systems and PLCs are both connected to the company intranet. Which of the following assumptions, if made by the penetration-testing team, is MOST likely to be
valid?
A penetration tester who is performing a physical assessment of a company’s security practices notices the company does not have any shredders inside the office building. Which of the following techniques would be BEST to use to gain confidential information?
A penetration tester who is performing an engagement notices a specific host is vulnerable to EternalBlue. Which of the following would BEST protect against this vulnerability?
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client’s cybersecurity tools? (Choose two.)
A penetration tester wrote the following comment in the final report: "Eighty-five percent of the systems tested were found to be prone to unauthorized access from the internet." Which of the following audiences was this message intended?
While performing the scanning phase of a penetration test, the penetration tester runs the following command:
........v -sV -p- 10.10.10.23-28
....ip scan is finished, the penetration tester notices all hosts seem to be down. Which of the following options should the penetration tester try next?
A penetration tester was brute forcing an internal web server and ran a command that produced the following output:
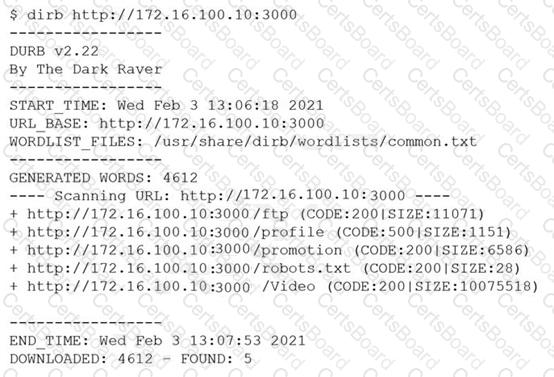
However, when the penetration tester tried to browse the URL http://172.16.100.10:3000/profile , a blank page was displayed.
Which of the following is the MOST likely reason for the lack of output?
An assessment has been completed, and all reports and evidence have been turned over to the client. Which of the following should be done NEXT to ensure the confidentiality of the client’s information?
Which of the following describes the reason why a penetration tester would run the command sdelete mimikatz. * on a Windows server that the tester compromised?
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?


