A penetration tester is performing a vulnerability scan on a large ATM network. One of the organization's requirements is that the scan does not affect legitimate clients' usage of the ATMs. Which of the following should the tester do to best meet the company's vulnerability scan requirements?
Which of the following tools can a penetration tester use to brute force a user password over SSH using multiple threads?
A penetration tester discovers a file, key.enc. on a shared drive and then executes the following command, which yields the following output:
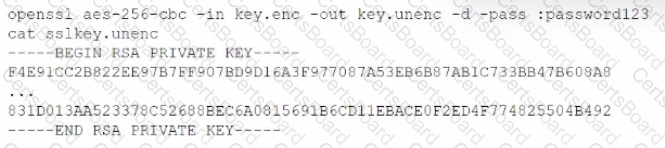
Which of the following are the best recommendations for the penetration tester to suggest? (Select two).
After successfully compromising a remote host, a security consultant notices an endpoint protection software is running on the host. Which of the following commands would be
best for the consultant to use to terminate the protection software and its child processes?
Which of the following would be the most efficient way to write a Python script that interacts with a web application?
Which of the following is the most important to include in the scope of a wireless security assessment?
During an assessment, a penetration tester was able Jo get access on all target servers by attempting authentication using a service account key that was published on the intranet site as part of a standard procedure. Which of the following should the penetration tester recommend for this type of finding?
A penetration tester noticed that an employee was using a wireless headset with a smartphone. Which of the following methods would be best to use to intercept the communications?
Which of the following OSSTM testing methodologies should be used to test under the worst conditions?


