Three access points have Ethernet that runs through the ceiling. One of the access points cannot reach the internet. Which of the following tools can help identify the issue?
Users cannot connect to an internal website with an IP address 10.249.3.76. A network administrator runs a command and receives the following output:
1 3ms 2ms 3ms 192.168.25.234
2 2ms 3ms 1ms 192.168.3.100
3 4ms 5ms 2ms 10.249.3.1
4 *
5 ’
6 *
7 •
Which of the following command-line tools is the network administrator using?
While troubleshooting connectivity issues, a junior network administrator is given explicit instructions to test the host's TCP/IP stack first. Which of the following commands should the network administrator run?
A firewall administrator is mapping a server's internal IP address to an external IP address for public use. Which of the following is the name of this function?
A critical infrastructure switch is identified as end-of-support. Which of the following is the best next step to ensure security?
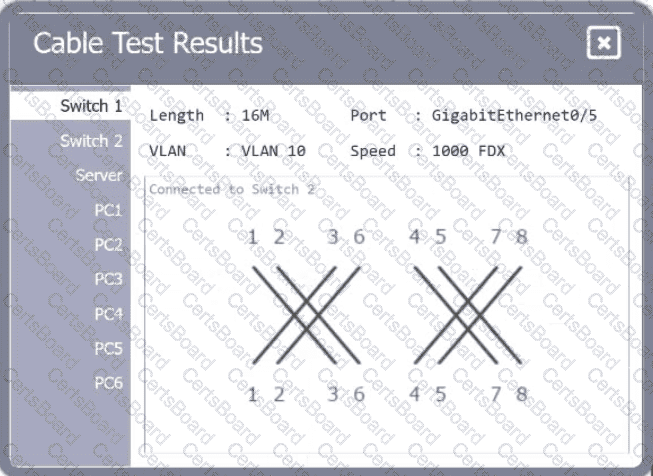
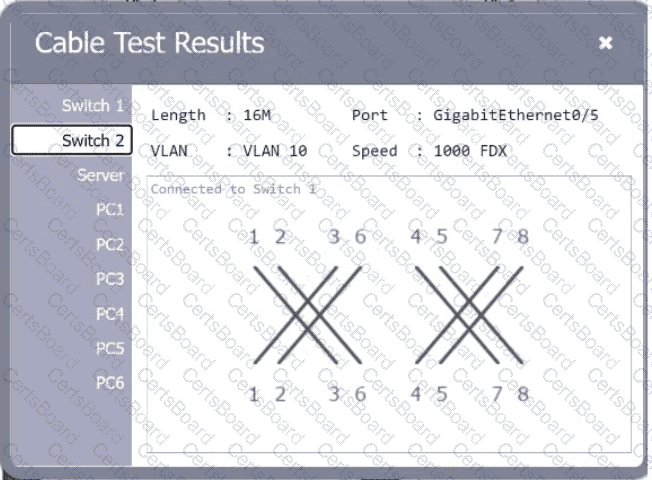
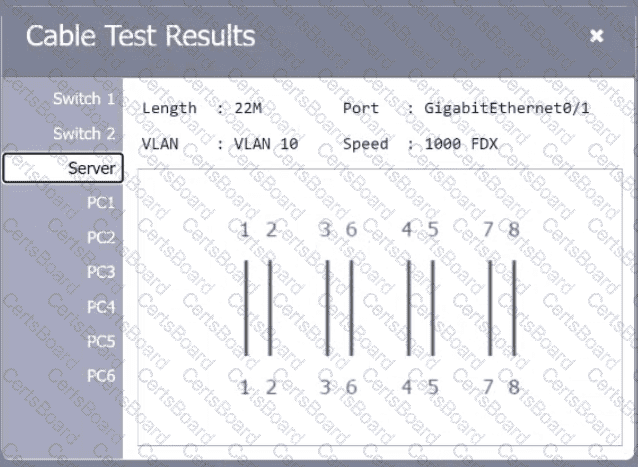
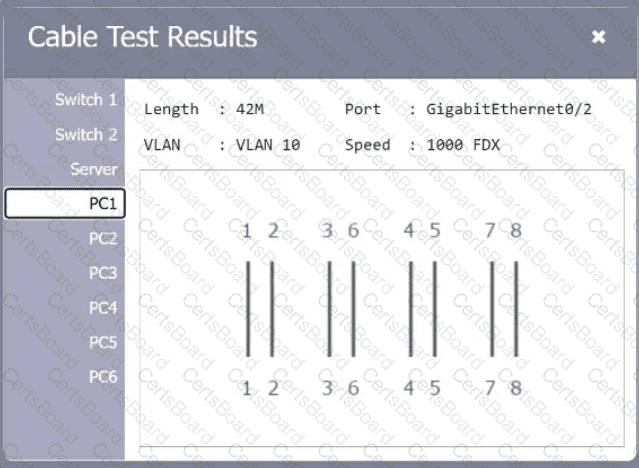
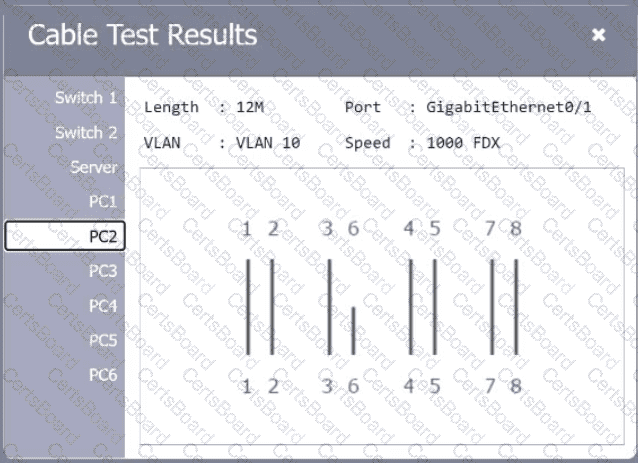
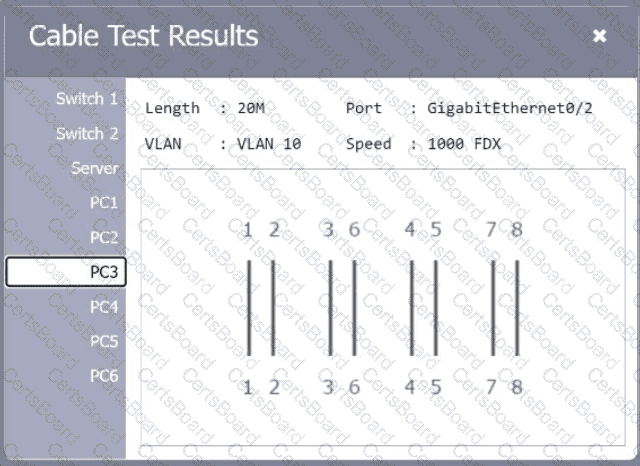
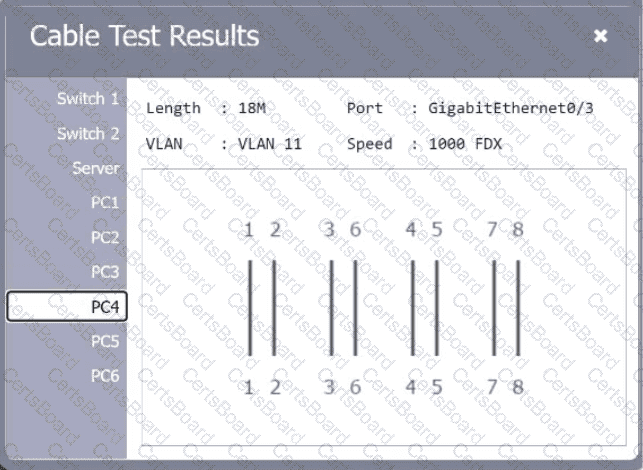
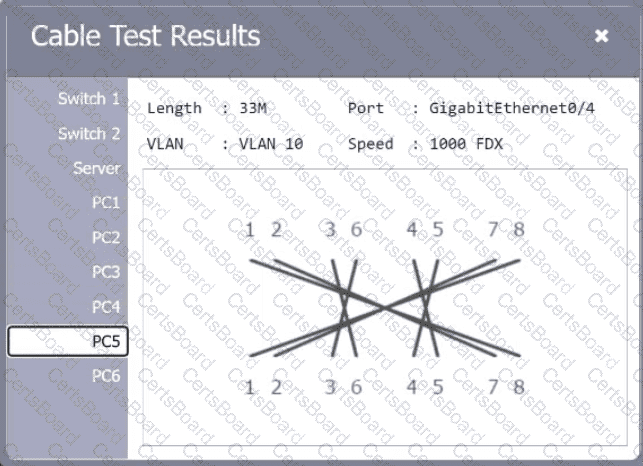
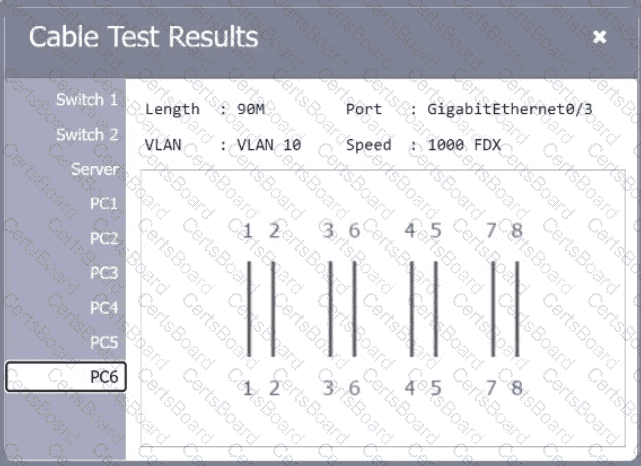
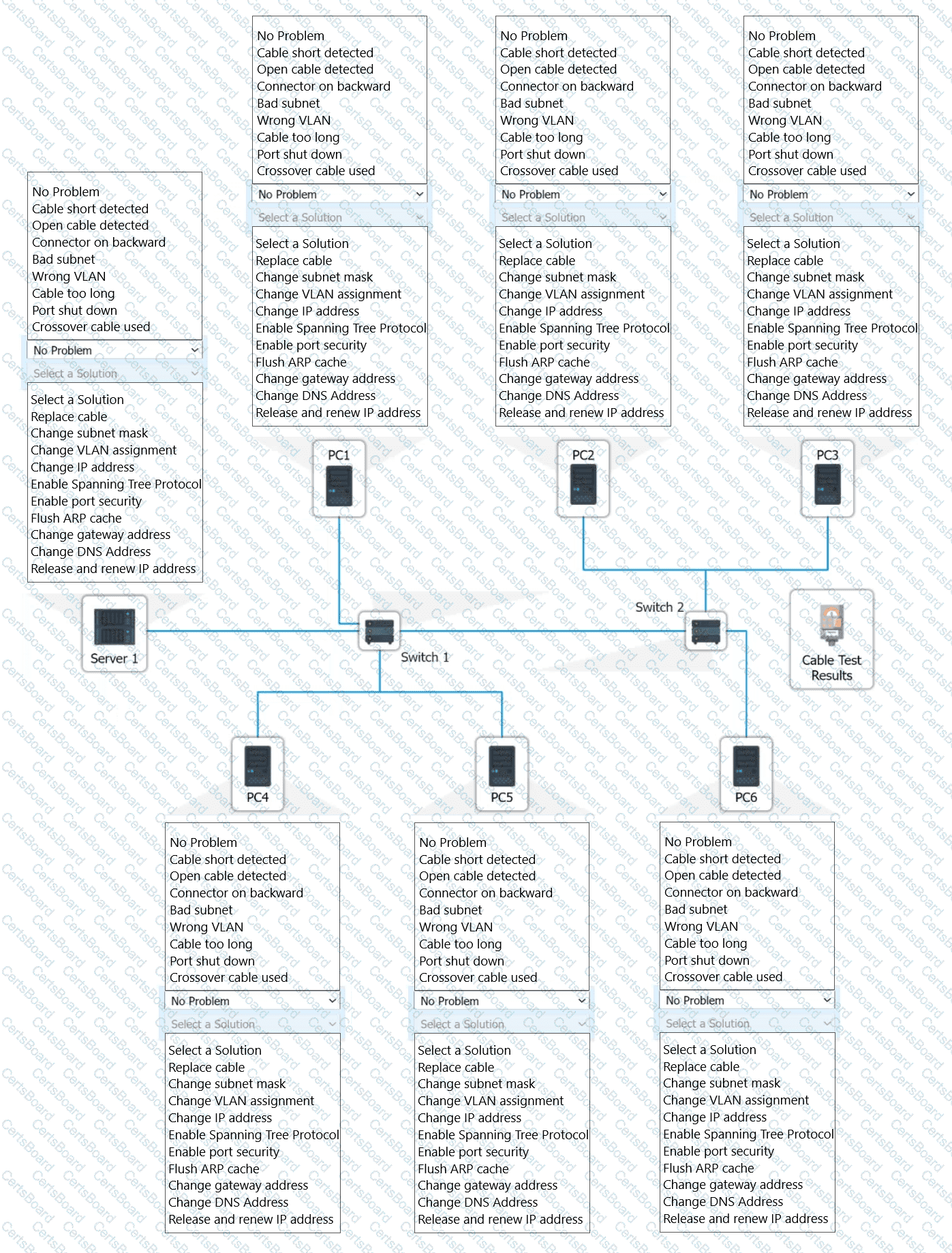
A network technician needs to resolve some issues with a customer's SOHO network. The
customer reports that some of the PCs are not connecting to the network, while others
appear to be working as intended.
INSTRUCTIONS
Troubleshoot all the network components.
Review the cable test results first, then diagnose by clicking on the appropriate PC,
server, and Layer 2 switch.
Identify any components with a problem and recommend a solution to correct each
problem.
If at any time you would like to bring back
the initial state of the simulation, please
click the Reset All button.
A user's home mesh wireless network is experiencing latency issues. A technician has:
•Performed a speed test.
•Rebooted the devices.
•Performed a site survey.
•Performed a wireless packet capture.
The technician reviews the following information:
The technician notices in the packet capture that frames were retransmitted. Which of the following is the most likely cause of the user's network issue?
A network technician needs to resolve some issues with a customer's SOHO network.
The customer reports that some of the devices are not connecting to the network, while others appear to work as intended.
INSTRUCTIONS
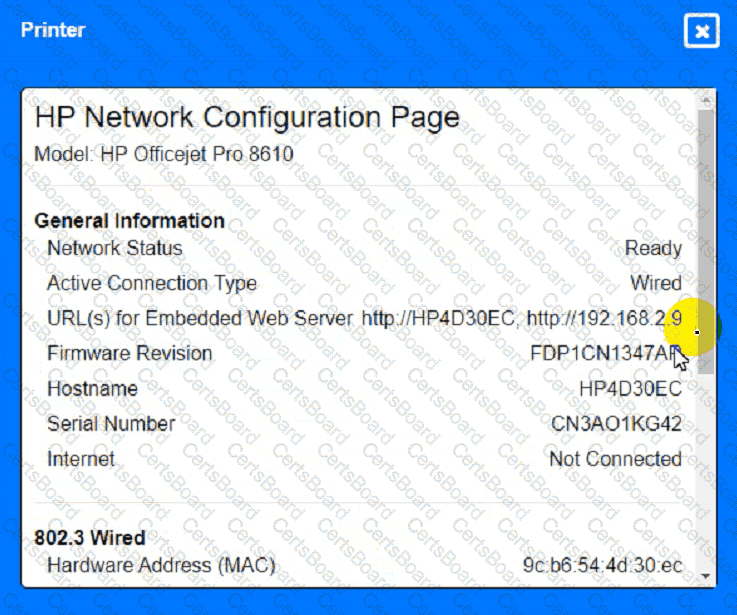
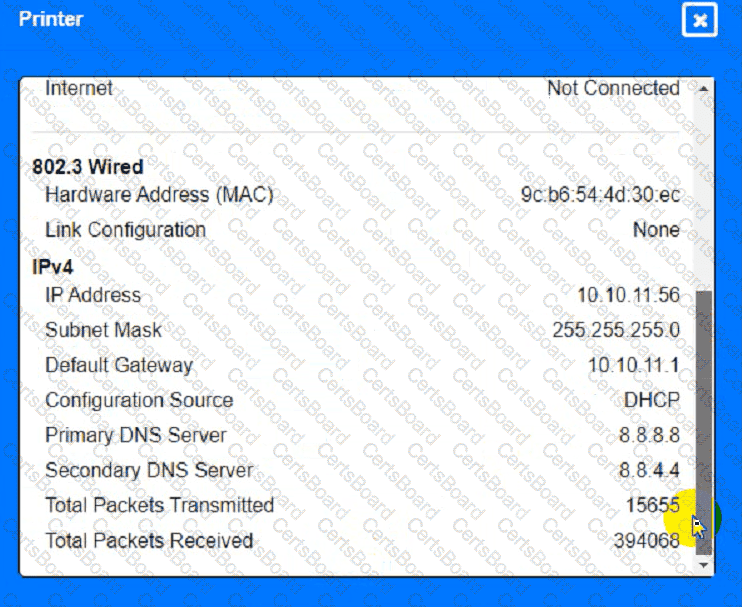
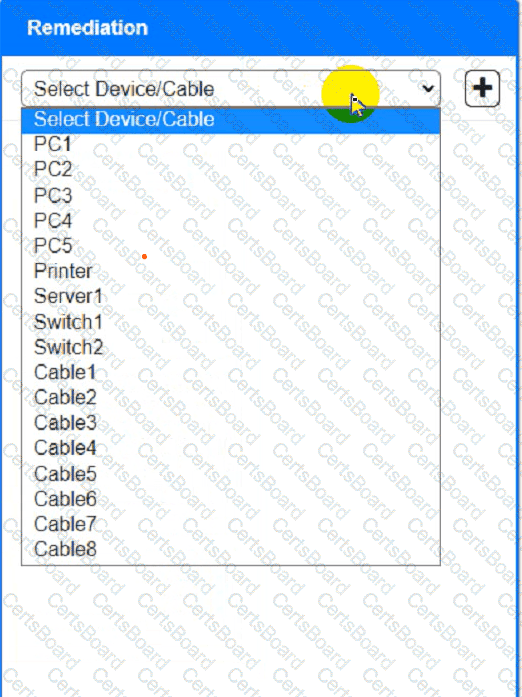
Troubleshoot all the network components and review the cable test results by Clicking on each device and cable.
Diagnose the appropriate component(s) by identifying any components with a problem and recommend a solution to correct each problem.
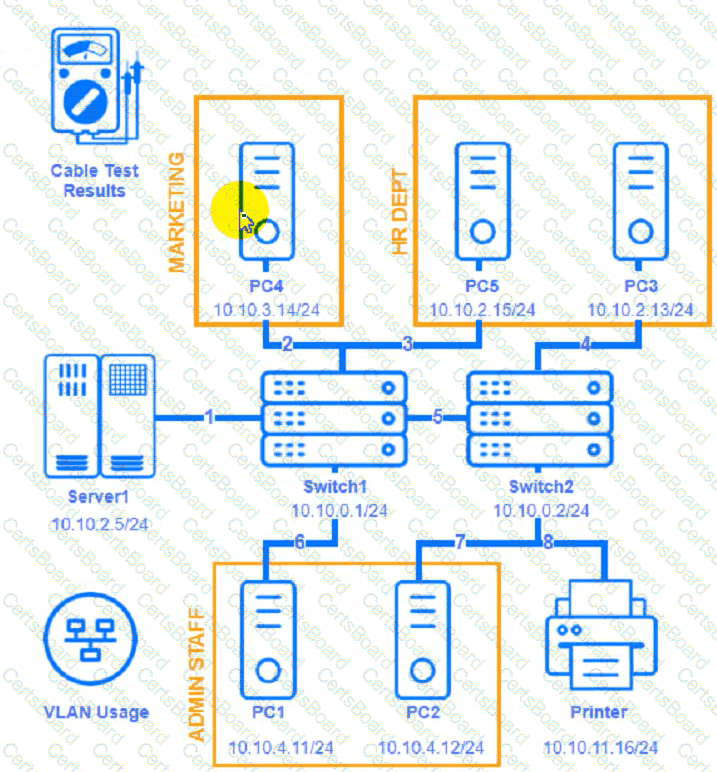





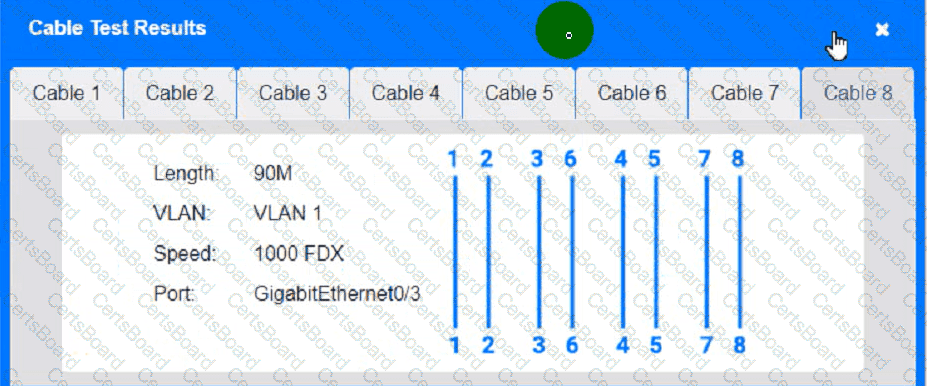
Cable Test Results:
Cable 1:
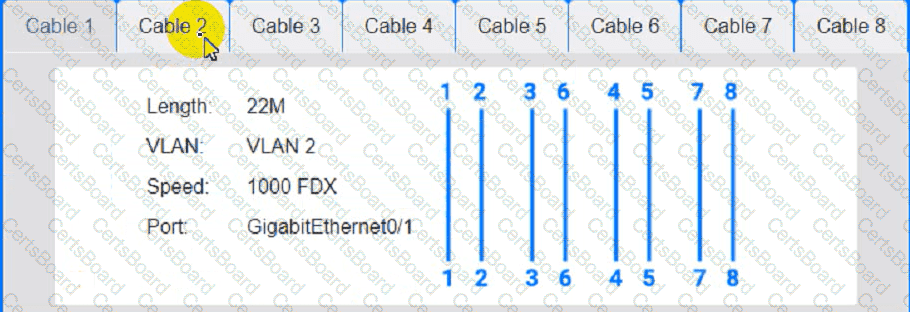
Cable 2:

Cable 3:
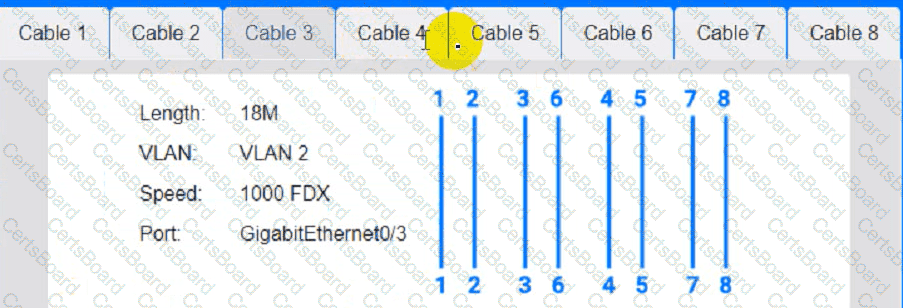
Cable 4:
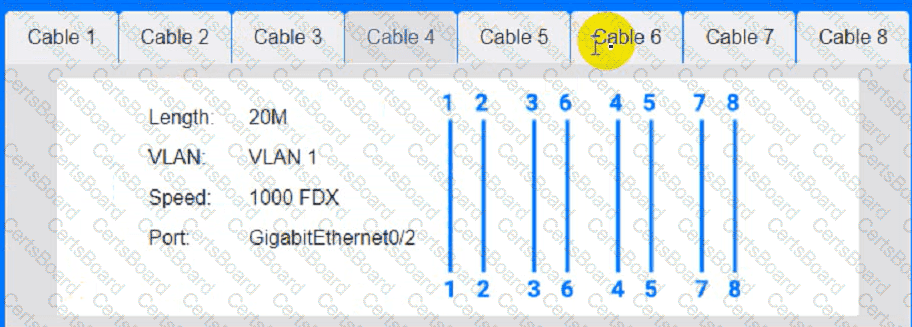
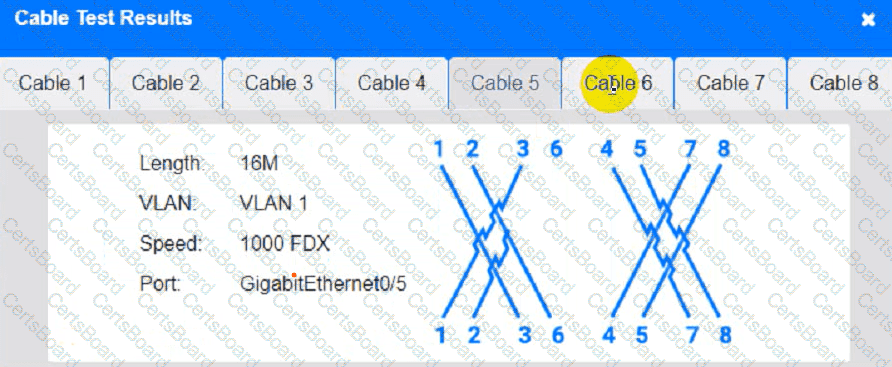
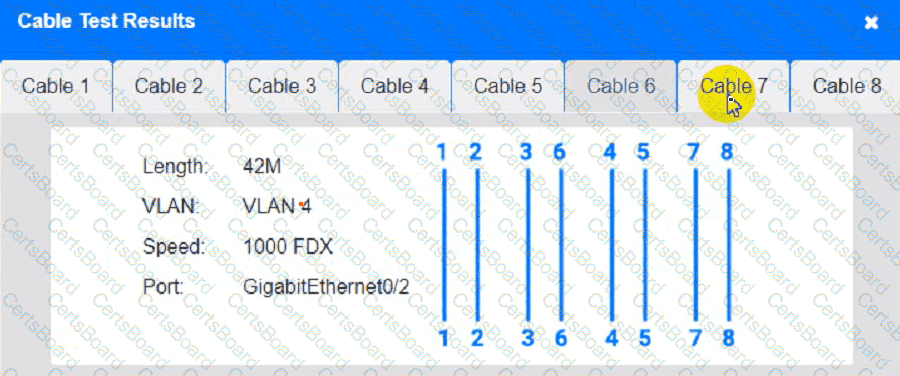

Users at a satellite office are experiencing issues when using videoconferencing. Which of the following should a technician focus on first to rectify these issues?
A network administrator wants to implement security zones in the corporate network to control access to only individuals inside of the corporation. Which of the following security zones is the best solution?


