Which of the following allows for theinterception of trafficbetween the source and destination?
A company recently rearranged some users' workspaces and moved several users to previously used workspaces. The network administrator receives a report that all of the users who were moved are having connectivity issues. Which of the following is the MOST likely reason?
Which of the following steps of the troubleshooting methodology should a technician take to confirm a theory?
After running a Cat 8 cable using passthrough plugs, an electrician notices that connected cables are experiencing a lot of cross talk. Which of the following troubleshooting steps should the electrician take first?
Which of the following steps in the troubleshooting methodology would be next after putting preventive measures in place?
Users are unable to access files on their department share located on file server 2.
The network administrator has been tasked with validating routing between networks
hosting workstation A and file server 2.
INSTRUCTIONS
Click on each router to review output, identify any issues, and configure the appropriate solution.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
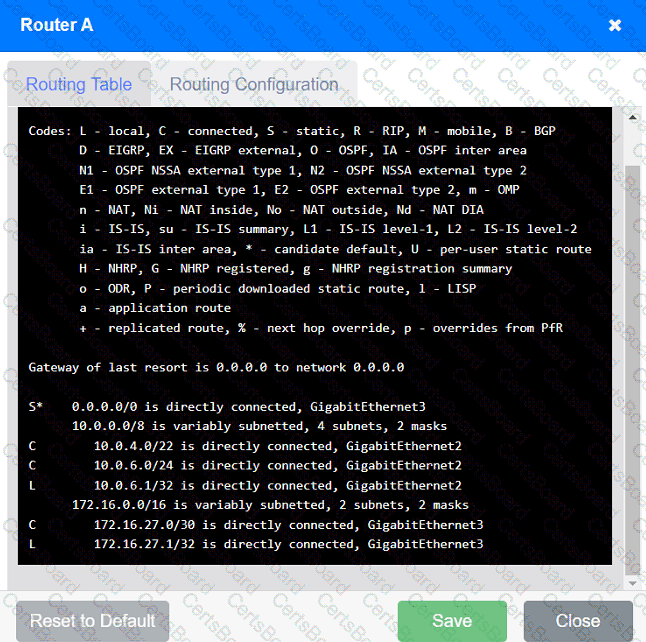
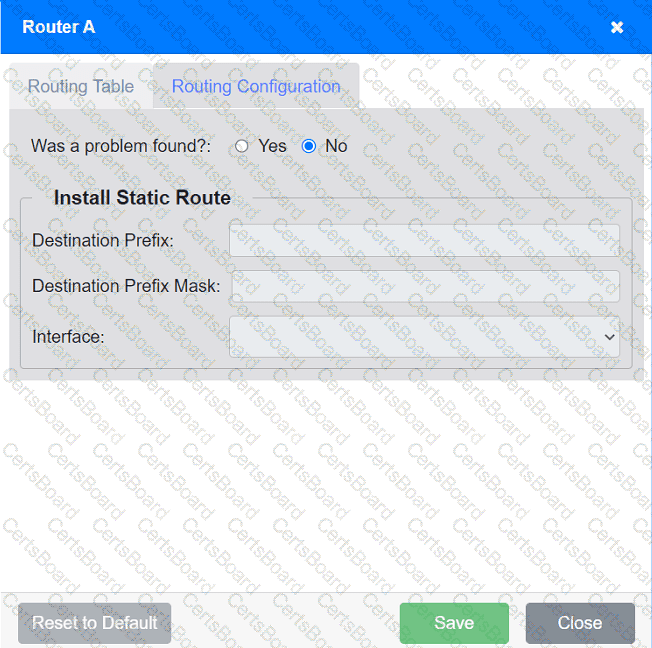
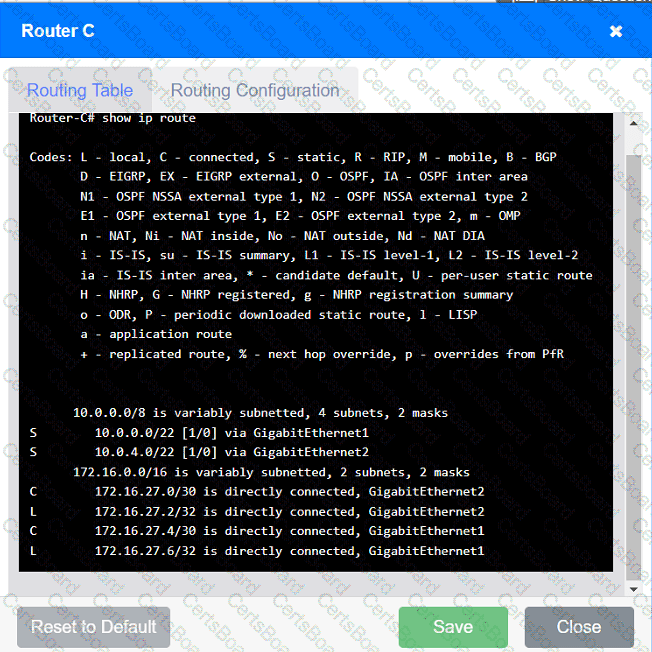
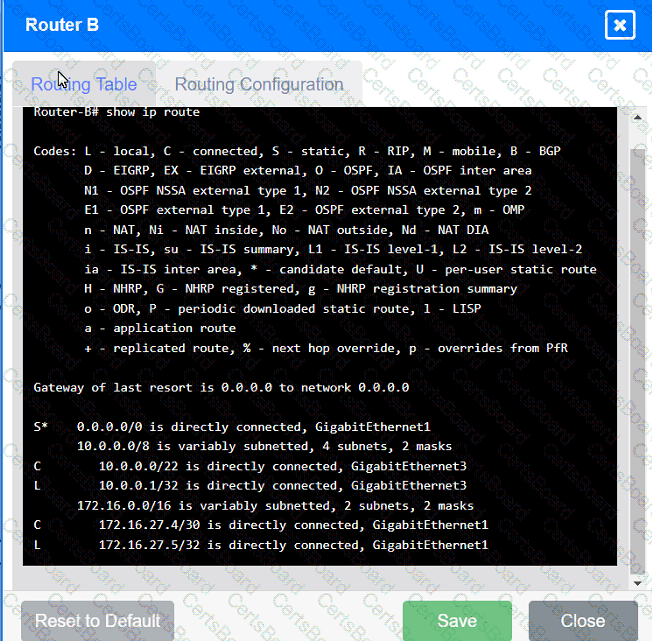
Which of the following protocol ports should be used to securely transfer a file?
An organization wants to ensure that incoming emails were sent from a trusted source. Which of the following DNS records is used to verify the source?


