Which part of the attack packet is matched by the blacklist to achieve attack prevention?
The ACK flood attack is defended by the load check. The principle is that the cleaning device checks the payload of the ACK packet. If the payloads are all consistent (if the payload content is all 1), the packet is discarded.
Because the policy in the traffic limiting policy does not restrict the deny rule, you do not need to use the deny rule.
What is the correct statement about the binding of local users to VPN instances?
What actions will be performed when the firewall hot standby sends the active/standby switchover?
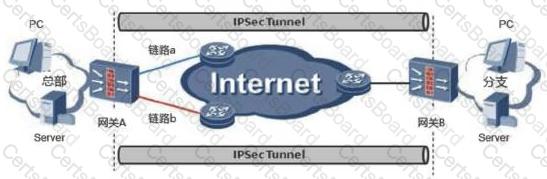
In the IPSec active/standby link backup application scenario, gateway B uses IPSec tunneling technology and gateway A to establish an IPSec VPN.
When using the optical bypass interface, the Bypass link has two working modes, automatic mode and forced mode.
The network of an enterprise is as follows. At this time, server A cannot access the web service of server B. The administrator performs troubleshooting and finds that there is no problem in the routing mode of firewall A. The corresponding routing table has been established, but the firewall mode of firewall A is set. error. What is the method used by the administrator to troubleshoot the problem?

The network administrator of a company discards traffic that exceeds the throughput of the device. The USG discards the traffic that exceeds the device throughput. The USG discards the traffic that exceeds the device throughput. The following command can achieve this function?


