An administrator can view the status of the device components by the following command: The status of the Slot3 board is Abnormal. What are the possible causes of the following faults?

An attack source will spoof the server and send a large number of SYN-ACK packets to the attacking target network or server. If the destination port of the packet is the TCP service port of the attacked server, the TCP protocol stack of the server will be abnormal. What is it?
L2TP is a tunneling protocol set up for transparent transmission of PPP packets between users and enterprise servers. Which of the following features are included?
Run the display ike sa command to check the IKE SA information. The following statement is correct?

The branch firewall of an enterprise is configured with NAT. As shown in the figure, USG_B is the NAT gateway. The USG_B is used to establish an IPSec VPN with the headquarters. Which parts of the USG_B need to be configured?

The constraints of the policy in the traffic limiting policy include quintuple, time period, user identity, and application protocol.
In the active/standby mode of the USG dual-system hot backup, the service interface works at Layer 3, and the upstream and downstream routers are connected. The administrator checks that the USG_A state has been switched to HRP_M[USG_A] and the USG_B state is also HRP_M[USG_B]. What are the most likely reasons?
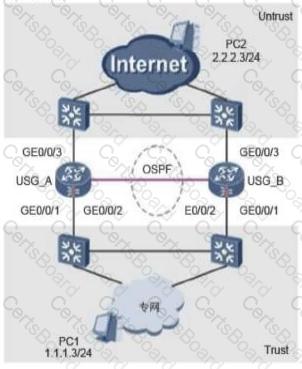
USG A and USG B are configured with a static BFD session. The following is true about the process of establishing and tearing down a BFD session.
Which of the following methods is used to switch between active and standby links in the IPSec backup and backup system?
The DHCP snooping function needs to maintain the binding table. What are the contents of the binding table?


