Refer to the exhibit.
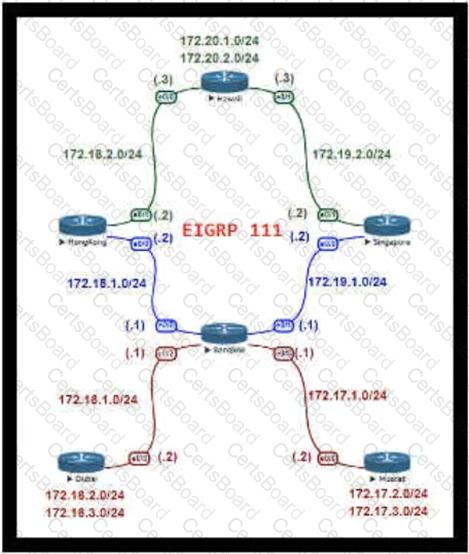
For Company XYZ Bangkok is using ECMP to reach the 172 20 2 0/24 network The company wants a design that would allow them to forward traffic from 172 16 2 0/24 toward 172 20 2 0/24 via the Singapore router as the preferred route The rest of the traffic should continue to use ECMP Which technology fulfills this design requirement?
You have been tasked with designing a data center interconnect to provide business continuity You want to encrypt the traffic over the DCI using IEEE 802 1AE MACsec to prevent the deployment of any firewall or IPS. Which two interconnect technologies support MACsec? (Choose two.)
Which DCI technology utilizes a “flood and learn” technique to populate the Layer2 forwarding table?
Which two benefits can software-defined networks provide to businesses? (Choose two.)
You are leading design discussions about IPv6 implementation into an existing Enterprise network A question is raised regarding older Layer 2 switches that exist in the network, and if any changes are required to these switches for successful IPv6 implementation Which two responses do you give? (Choose two.)
SDN emerged as a technology trend that attracted many industries to move from traditional networks to SDN. Which challenge is solved by SDN for cloud service providers?
As part of workspace digitization, a large enterprise has migrated all their users to Desktop as a Sen/ice (DaaS), by hosting the backend system in their on-premises data center. Some of the branches have started to experience disconnections to the DaaS at periodic intervals, however, local users in the data center and head office do not experience this behavior. Which technology can be used to mitigate this issue?
Refer to the exhibit.
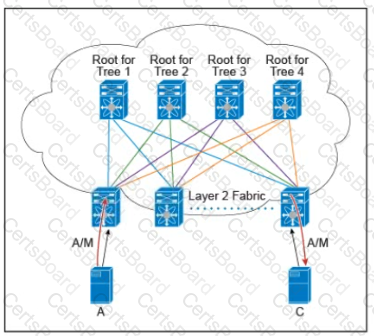
There are multiple trees in the Cisco FabricPath All switches in the Layer 2 fabric share the same view of each tree. Which two concepts describe how the multicast traffic is load-balanced across this topology? (Choose two )
A network attacker exploits application flaws to compromise critical systems in the organization with these objectives:
• Obtain sensitive data and export the data out of the network.
• Compromise developer and administrator credentials to potentially
What is the next step after application discovery is completed in Zero Trust networkings
Company XYZ is designing the IS-IS deployment strategy for their multiarea IS-IS domain. They want IS-IS neighbour relationships to be minimized on each network segment and want to optimize the size of the IS-IS LSDB on each router. Which can design can be used to meet these requirements?


