You were tasked to enhance the security of a network with these characteristics:
• A pool of servers is accessed by numerous data centers and remote sites
• The servers are accessed via a cluster of firewalls
• The firewalls are configured properly and are not dropping traffic
• The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology should you recommend to enhance security by limiting traffic that could originate from a hacker compromising a workstation and redirecting flows at the servers?
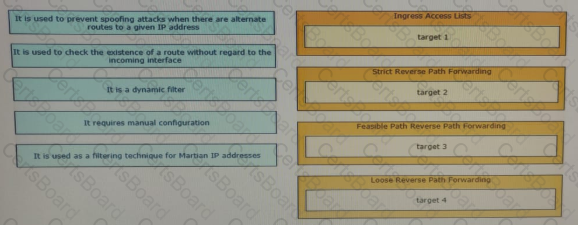
Drag and drop the design characteristics from the left onto the correct network filter techniques on the right. Not all options are used.
What is a web-based model in which a third-party provider hosts applications that are available to customers over the Internet?
Which development model is closely associated with traditional project management?
In the wake of a security compromise incident where the internal networks were breached by an outside attacker at the perimeter of the infrastructure, an enterprise is now evaluating potential measures that can help protect against the same type of incident in the future. What are two design options that can be employed? (Choose two)
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?
Various teams in different organizations within an enterprise are preparing low-level design documents to capture network parameters using a Waterfall project model:
• hardware sizing and power consumption
• Layer 2 and layer 3 services parameters
• configuration of all control plane protocols
Input from relevant stakeholders was captured at the start of the project, and the project scope has been defined based on the parameters above. What impact will it have on documentation and project deliverables if the stakeholders ask to have changes carried out in the network before the information has been captured?
While designing a switched topology, in which two options is UplinkFast recommended? (Choose two )
A private cloud is accessed over the private IT network infrastructure that is potentially vulnerable to violations, data leaks, and man-in- the-middle attacks. The security team is evaluating the following solutions to address the challenges:
•Encrypt data at rest and in transition.
•Use strong identity and access management (IAM) capabilities.
•Communicate the inherent data security risks to your customers and end-users.
Assuming that adoption of a hybrid cloud model is likely to occur within the next 12 months, which two solutions can also help provide protection in a hybrid cloud environment? (Choose two.)


