As a network administrator, you have implemented WPA2 encryption in your corporate wireless network. The WPA2's _________integrity check mechanism provides security against a replay attack
Which of the following standards does a cloud service provider has to comply with, to protect the privacy of its customer’s personal information?
Which of the following NIST incident category includes any activity that seeks to access or identify a federal agency computer, open ports, protocols, service or any combination for later exploit?
Sam, a network administrator is using Wireshark to monitor the network traffic of the organization. He wants to detect TCP packets with no flag set to check for a specific attack attempt. Which filter will he use to view
the traffic?
Who is responsible for executing the policies and plans required for supporting the information technology and computer systems of an organization?
A company wants to implement a data backup method which allows them to encrypt the data ensuring its security as well as access at any time and from any location. What is the appropriate backup method that
should be implemented?
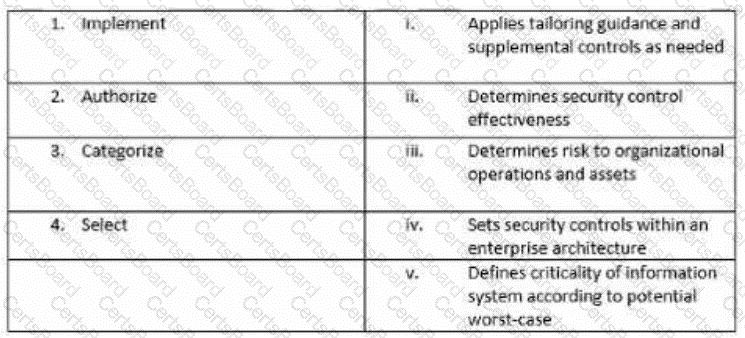
Match the following NIST security life cycle components with their activities:
-----------is a group of broadband wireless communications standards for Metropolitan Area Networks (MANs)
John has implemented________in the network to restrict the limit of public IP addresses in his organization and to enhance the firewall filtering technique.


