Which of the following is the MOST cost-effective version of Windows 10 that allows remote access through Remote Desktop?
During a recent flight an executive unexpectedly received several dog and cat pictures while trying to watch a movie via in-flight Wi-Fi on an iPhone. The executive has no records of any contacts sending pictures like these and has not seen these pictures before. To BEST resolve this issue, the executive should:
An executive has contacted you through the help-desk chat support about an issue with a mobile device.
Assist the executive to help resolve the issue.
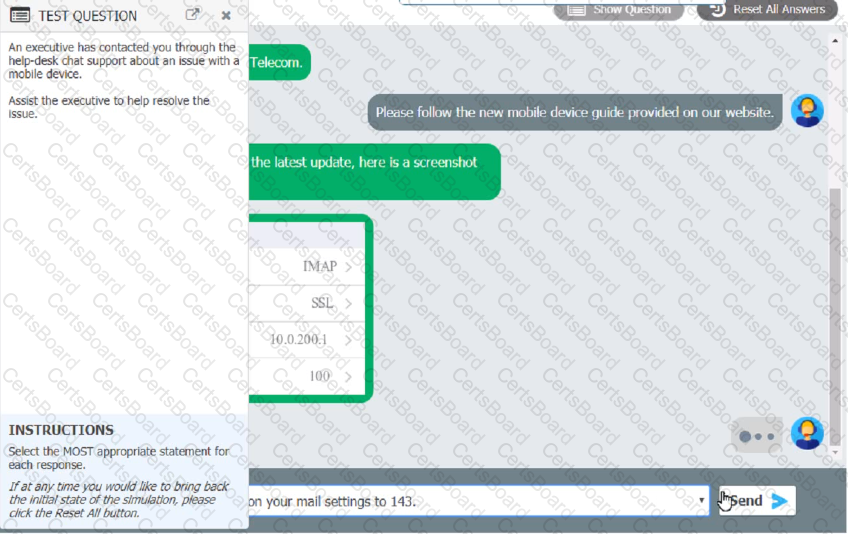
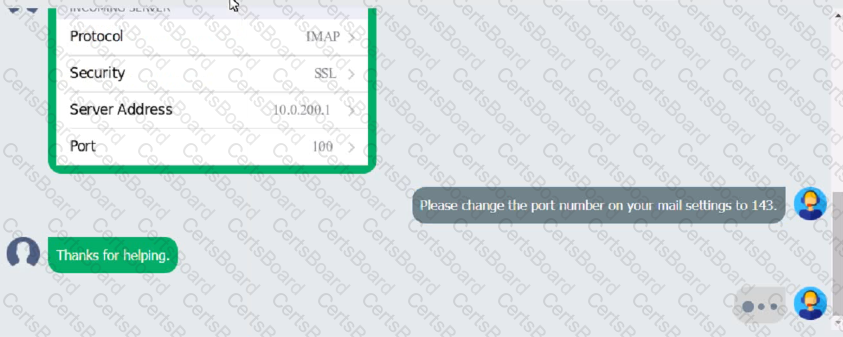
Which of the following should be done NEXT?
A technician suspects the boot disk of a user's computer contains bad sectors. Which of the following should the technician verify in the command prompt to address the issue without making any changes?
A change advisory board just approved a change request. Which of the following is the MOST likely next step in the change process?
A new spam gateway was recently deployed at a small business However; users still occasionally receive spam. The management team is concerned that users will open the messages and potentially
infect the network systems. Which of the following is the MOST effective method for dealing with this Issue?
A technician has an external SSD. The technician needs to read and write to an external SSD on both Macs and Windows PCs. Which of the following filesystems is supported by both OS types?
A user is having issues with document-processing software on a Windows workstation. Other users that log in to the same device do not have the same issue.
Which of the following should a technician do to remediate the issue?
A technician wants to mitigate unauthorized data access if a computer is lost or stolen. Which of the following features should the technician enable?
A new service desk is having a difficult time managing the volume of requests. Which of the following is the BEST solution for the department?
A technician is tasked with configuring a computer for a visually impaired user. Which of the following utilities should the technician use?
A team of support agents will be using their workstations to store credit card data. Which of the following should the IT department enable on the workstations in order to remain compliant with common regulatory controls? (Select TWO).
A user is unable to log in to the network. The network uses 802.1X with EAP-TLS to authenticate on the wired network. The user has been on an extended leave and has not logged in to the computer in several months. Which of the following is causing the login issue?
A technician connects an additional monitor to a PC using a USB port. The original HDMI monitor is mounted to the left of the new monitor. When moving the mouse to the right from the original monitor to the new monitor, the mouse stops at the end of the screen on the original monitor. Which
of the following will allow the mouse to correctly move to the new monitor?
A desktop support technician is tasked with migrating several PCs from Windows 7 Pro to Windows 10 Pro, The technician must ensure files and user preferences are retained, must perform the operation locally, and should migrate one station at a time. Which of the following methods would be MOST efficient?


