Which two should you determine to ensure that your client can successfully maintain and administer Perspectives post go-live? (Choose two.)
You are remediating access incidents in Advanced Access Controls (AAC), and have just completed the remediation of a segregation of duties conflict for users in Fusion Security by removing the conflicting access from the users.
What status do you set for the incident in AAC?
At the last step of initiating assessments, the assessment manager sees who the assessment participants are (to complete, review, and approve the assessments). If the assessment manager wants to change the participant, who completes the assessment, what should he or she do?
You have created security roles for the Procure-to-Pay (P2P) Control Manager for the EMEA region in your client’s organization. But, there are two problems with his or her security configuration.
Problem 1: This person should not receive notifications to complete control assessments, but currently he or she does.
Problem 2: Also, although he or she has access to controls associated with EMEA, he or she is unable to access controls created for individual regions within EMEA.
You have given him or her the following job role:
Which two actions need to be taken to correct the problems? (Choose two.)
You are validating your customer’s import template before import. The customer requires that all controls be set up so they are noted to be used for the Audit Test assessment type. How do you verify that this has been done?
You have built a transaction model to identify possible duplicate charges between invoicing and expense credit cards. The model logic already includes two standard filters that identify amounts and suppliers that are the same or similar, as shown:
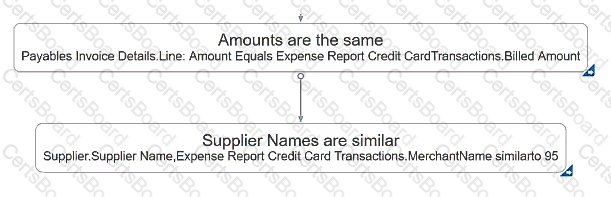
Which additional date filter will further refine the set of duplicate charges found?
During implementation, you created a risk object and successfully mapped it to a control object. The client’s Risk Owner is able to access the risk but not the control.
Why did this happen?
Which filter can be used to identify expense reports that contain suspicious expense type combinations, such as, a report for a single trip that contains taxi, car rental, and mileage expenses?


