Which option is required to Activate/Retrieve a Device Management License on the M-100 Appliance after the Auth Codes have been activated on the Palo Alto Networks Support Site?
XYZ Corporation has a legacy environment with asymmetric routing. The customer understands that Palo Alto Networks firewalls can support asymmetric routing with redundancy. Which two features must be enabled to meet the customer's requirements? (Choose two.)
Which three platform components can identify and protect against malicious email links? (Choose three.)
Which two features can be enabled to support asymmetric routing with redundancy on a Palo
Alto networks next-generation firewall (NGFW)? (Choose two.)
Which CLI allows you to view the names of SD-WAN policy rules that send traffic to the specified virtual SD-WAN interface, along with the performance metrics?
A)
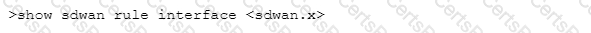
B)
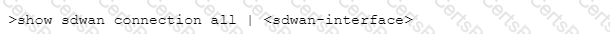
C)
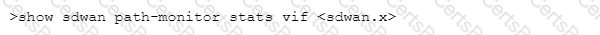
D)
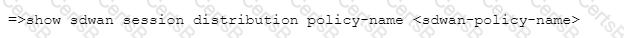
When the Cortex Data Lake is sized for Traps Management Service, which two factors should be considered? (Choose two.)
Which three of the following actions must be taken to enable Credential Phishing Prevention? (Choose three.)
A potential customer requires an NGFW solution which enables high-throughput, low-latency network security, all while incorporating unprecedented features and technology. They need a solution that solves the performance problems that plague today's security infrastructure.
Which aspect of the Palo Alto Networks NGFW capabilities can you highlight to help them address the requirements?
An SE is preparing an SLR report for a school and wants to emphasize URL filtering capabilities because the school is concerned that its students are accessing inappropriate websites. The URL categories being chosen by default in the report are not highlighting these types of websites. How should the SE show the customer the firewall can detect that these websites are being accessed?


