Which statement best describes the business value of Palo Alto Networks Zero Touch Provisioning (ZTP)?
WildFire can discover zero-day malware in which three types of traffic? (Choose three)
Which three features are used to prevent abuse of stolen credentials? (Choose three.)
Which two components must be configured within User-ID on a new firewall that has been implemented? (Choose two.)
in which step of the Palo Alto Networks Five-Step Zero Trust Methodology would an organization's critical data, applications, assets, and services (DAAS) be identified?
Which CLI command will allow you to view latency, jitter and packet loss on a virtual SD-WAN interface?
A)
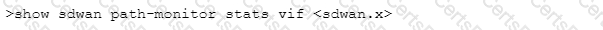
B)
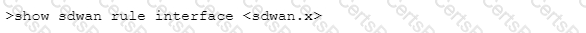
C)

D)

A customer with a fully licensed Palo Alto Networks firewall is concerned about threats based on domain generation algorithms (DGAS).
Which Security profile is used to configure Domain Name Security (DNS) to Identity and block
previously unknown DGA-based threats in real time?
What are two benefits of using Panorama for a customer who is deploying virtual firewalls to secure data center traffic? (Choose two.)


