Exhibit
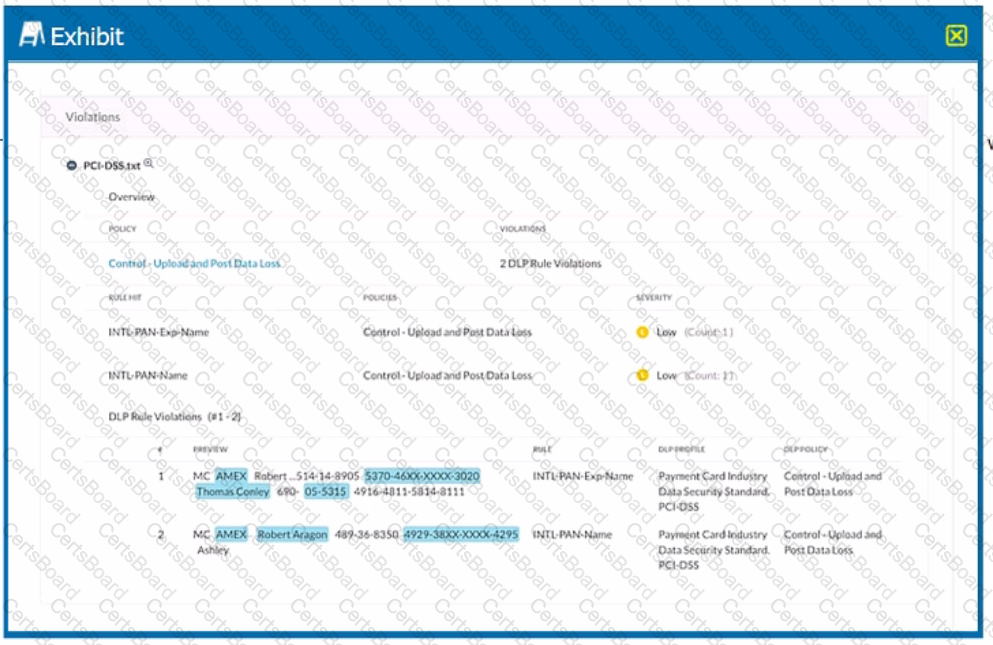
Which portion of the interface shown in the exhibit allows an administrator to set severity, assign ownership, track progress, and perform forensic analysis with excerpts of violating content?
Which compliance standard should a company consider if both controllers and processors have legal entities in the EU?
You need to locate events for specific activities such as "edit" or "login successful" in a cloud application.
In which SkopeIT Events & Alerts page would this information be found?
Which three technologies describe the primary cloud service models as defined by the National Institute of Standards and Technology (NIST)? (Choose three.)
Click the Exhibit button.
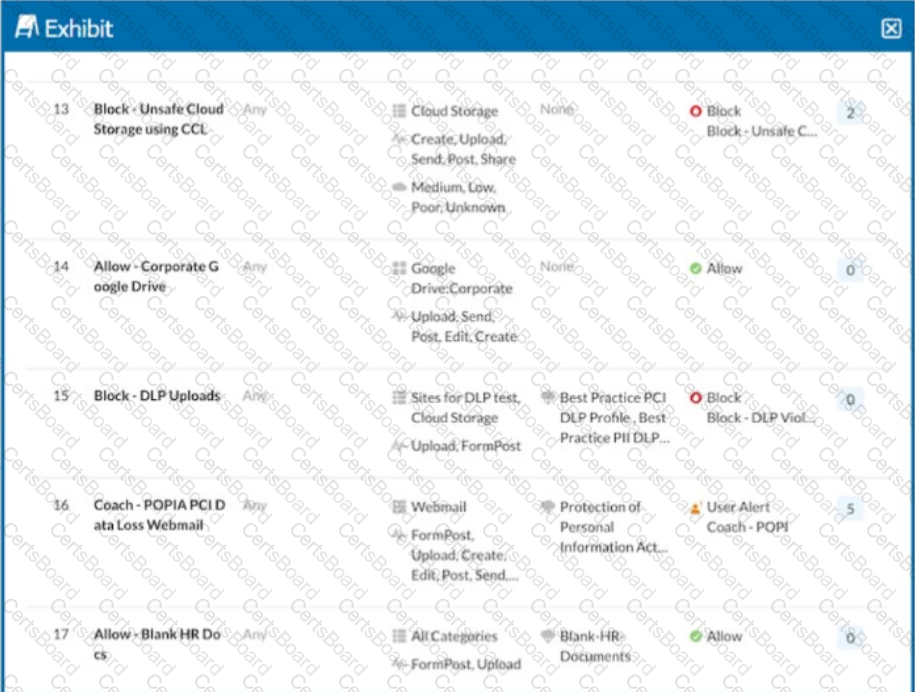
A user is uploading a file containing PCI-DSS data to the corporate Google Drive instance. You notice that the upload is not blocked by the policy shown in the exhibit. Which statement is correct in this scenario?
What are two correct methods to gather logs from the Netskope Client? (Choose two.)
Click the Exhibit button.

You configured a set of Cloud Firewall policies as shown in the exhibit and changed your Steering Configuration to All Traffic for Group A and Group B. Users in Group A report that they are unable to access a third-party server using TCP port 3389. Referring to the exhibit, which action correctly describes how you would allow these connections without allowing unnecessary access?
You are working with traffic from applications with pinned certificates. In this scenario, which statement is correct?


