As an administrator, you need to configure the Netskope Admin UI to be accessible by specific IP addresses and to display a custom message after the admin users have been authenticated.
Which two statements are correct in this scenario? (Choose two.)
You determine that a business application uses non-standard HTTPS ports. You want to steer all HTTPS traffic for this application and have visibility and control over user activities.
Which action will allow you to accomplish this task?
Click the Exhibit button.
Referring to the exhibit, which statement accurately describes the difference between Source IP (Egress) and Source IP (User) address?
What information is displayed in an application's Cloud Confidence Index (CCI) page? (Choose two.)
Your company started deploying the latest version of the Netskope Client and you want to track the progress and device count using Netskope.
Which two statements are correct in this scenario? (Choose two.)
Click the Exhibit button.
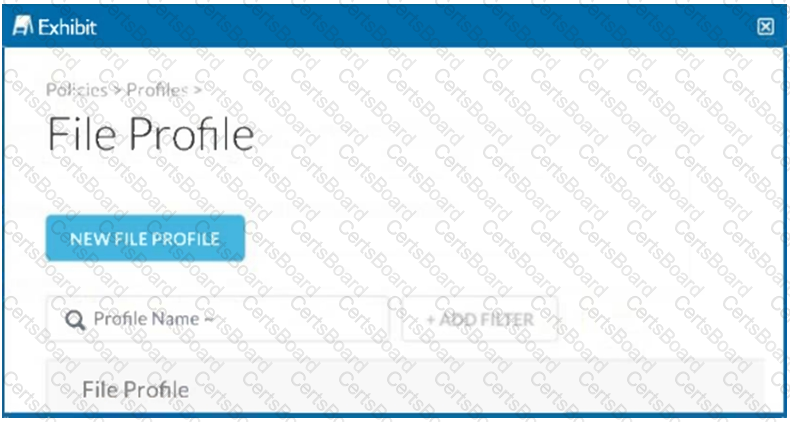
What are two use cases where the parameter shown in the exhibit is required? (Choose two.)
An administrator has created a DLP rule to search for text within documents that match a specific pattern. After creating a Real-time Protection Policy to make use of this DLP rule, the administrator suspects the rule is generating false positives.
Within the Netskope tenant, which feature allows administrators to review the data that was matched by the DLP rule?
A user has performed a bulk delete activity. In this scenario, which Netskope feature monitors potential risky users for a malicious activity that would cause data loss?
In the Skope IT interface, which two event tables would be used to label a cloud application instance? (Choose two.)


