A network technician is investigating an issue with a desktop that is not connecting to the network. The desktop was connecting successfully the previous day, and no changes were made to the environment. The technician locates the switchport where the device is connected and observes the LED status light on the switchport is not lit even though the desktop is turned on Other devices that arc plugged into the switch are connecting to the network successfully Which of the following is MOST likely the cause of the desktop not connecting?
A network administrator needs to implement an HDMI over IP solution. Which of the following will the network administrator MOST likely use to ensure smooth video delivery?
A network technician is installing an analog desk phone for a new receptionist After running a new phone line, the technician now needs to cnmp on a new connector. Which of the following connectors would MOST likely be used in this case?
Which of the following policies is MOST commonly used for guest captive portals?
During the security audit of a financial firm the Chief Executive Officer (CEO) questions why there are three employees who perform very distinct functions on the server. There is an administrator for creating users another for assigning the users lo groups and a third who is the only administrator to perform file rights assignment Which of the following mitigation techniques is being applied'
A SaaS provider has decided to leave an unpatched VM available via a public DMZ port. With which of the following concepts is this technique MOST closely associated?
Which of the following attacks encrypts user data and requires a proper backup implementation to recover?
A network technician needs to correlate security events to analyze a suspected intrusion. Which of the following should the technician use?
A technician is troubleshooting a workstation's network connectivity and wants to confirm which switchport corresponds to the wall jack the PC is using Which of the following concepts would BEST help the technician?
Which of the following protocol types describes secure communication on port 443?
There are two managed legacy switches running that cannot be replaced or upgraded. These switches do not support cryptographic functions, but they are password protected. Which of the following should a network administrator configure to BEST prevent unauthorized access?
Given the following output:
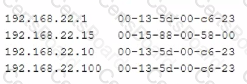
Which of the following attacks is this MOST likely an example of?
Which of the following technologies allows traffic to be sent through two different ISPs to increase performance?
Which of the following protocols will a security appliance that is correlating network events from multiple devices MOST likely rely on to receive event messages?
A network technician has multimode fiber optic cable available in an existing IDF. Which of the following Ethernet standards should the technician use to connect the network switch to the existing fiber?