According to the log shown in the exhibit, you notice the IPsec session is not establishing.
What is the reason for this behavior?
Your company wants to use the Juniper Seclntel feeds to block access to known command and control servers, but they do not want to use Security Director to manage the feeds.
Which two Juniper devices work in this situation? (Choose two)
You have a webserver and a DNS server residing in the same internal DMZ subnet. The public Static NAT addresses for
the servers are in the same subnet as the SRX Series devices internet-facing interface. You implement DNS doctoring to
ensure remote users can access the webserver.Which two statements are true in this scenario? (Choose two.)
The monitor traffic interface command is being used to capture the packets destined to and the from the SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
Exhibit
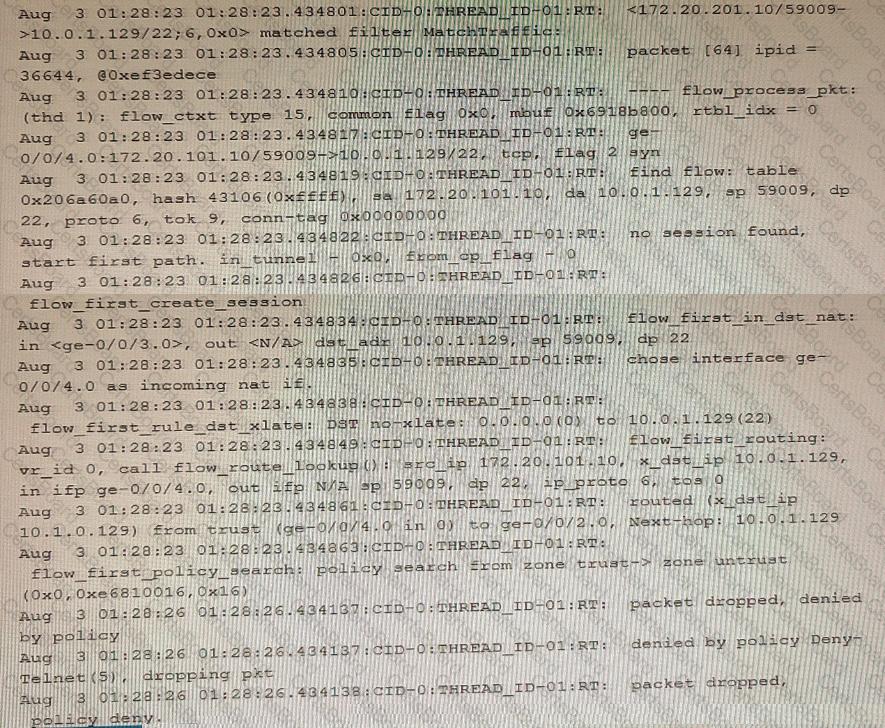
Which two statements are correct about the output shown in the exhibit. (Choose two.)
You want to configure a threat prevention policy.
Which three profiles are configurable in this scenario? (Choose three.)
Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data traffic. How many IKE security associations are required between the IPsec peers in this scenario?
you are connecting two remote sites to your corporate headquarters site. You must ensure that traffic
passes corporate headquarter.
In this scenario, which VPN should be used?


