You want to identify potential threats within SSL-encrypted sessions without requiring SSL proxy to decrypt the session contents. Which security feature achieves this objective?
Your Source NAT implementation uses an address pool that contains multiple IPv4 addresses Your users report that when they establish more than one session with an external application, they are prompted to authenticate multiple times External hosts must not be able to establish sessions with internal network hosts
What will solve this problem?
You want to enforce I DP policies on HTTP traffic.
In this scenario, which two actions must be performed on your SRX Series device? (Choose two )
Your organization has multiple Active Directory domain to control user access. You must ensure that security polices are passing traffic based upon the user’s access rights.
What would you use to assist your SRX series devices to accomplish this task?
You issue the command shown in the exhibit.
Which policy will be active for the identified traffic?
Exhibit
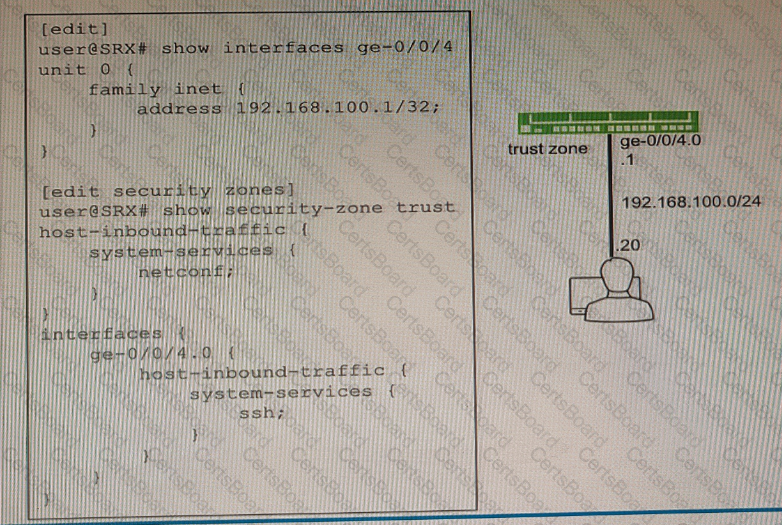
You are not able to ping the default gateway of 192.168 100 1 (or your network that is located on your SRX Series firewall.
Referring to the exhibit, which two commands would correct the configuration of your SRX Series device? (Choose two.)
A)

B)

C)

D)

Exhibit
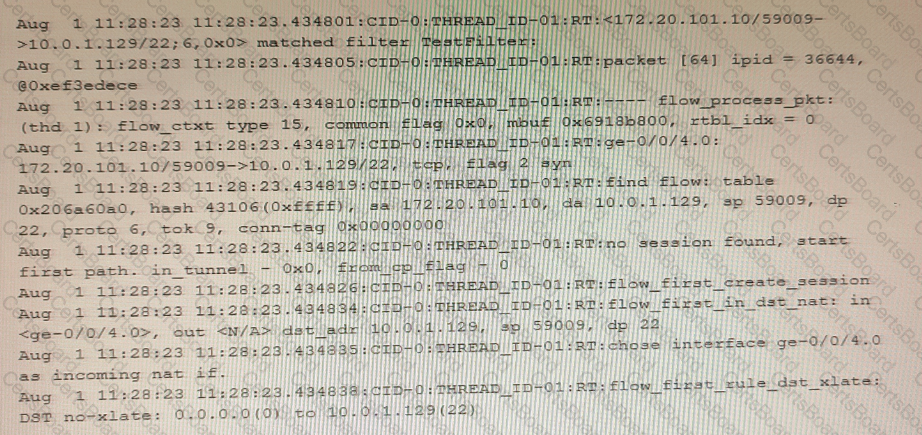
The exhibit shows a snippet of a security flow trace.
In this scenario, which two statements are correct? (Choose two.)


