Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It provides network security, virtualization, cloud computing, network hardware, network management software, and networking technologies.
The company's recognition has increased drastically since gaining ISO/IEC 27001 certification. The certification confirmed the maturity of UpNefs operations and its compliance with a widely recognized and accepted standard.
But not everything ended after the certification. UpNet continually reviewed and enhanced its security controls and the overall effectiveness and efficiency of the ISMS by conducting internal audits. The top management was not willing to employ a full-time team of internal auditors, so they decided to outsource the internal audit function. This form of internal audits ensured independence, objectivity, and that they had an advisory role about the continual improvement of the ISMS.
Not long after the initial certification audit, the company created a new department specialized in data and storage products. They offered routers and switches optimized for data centers and software-based networking devices, such as network virtualization and network security appliances. This caused changes to the operations of the other departments already covered in the ISMS certification scope.
Therefore. UpNet initiated a risk assessment process and an internal audit. Following the internal audit result, the company confirmed the effectiveness and efficiency of the existing and new processes and controls.
The top management decided to include the new department in the certification scope since it complies with ISO/IEC 27001 requirements. UpNet announced that it is ISO/IEC 27001 certified and the certification scope encompasses the whole company.
One year after the initial certification audit, the certification body conducted another audit of UpNefs ISMS. This audit aimed to determine the UpNefs ISMS fulfillment of specified ISO/IEC 27001 requirements and ensure that the ISMS is being continually improved. The audit team confirmed that the certified ISMS continues to fulfill
the requirements of the standard. Nonetheless, the new department caused a significant impact on governing the management system. Moreover, the certification body was not informed about any changes. Thus, the UpNefs certification was suspended.
Based on the scenario above, answer the following question:
UpNet outsourced the internal audit function, as provided in scenario 9. Does it impact the internal audit process?
Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector since September 2010. The company has a network of 30 branches with over 100 ATMs across the country.
Operating in a highly regulated industry, EsBank must comply with many laws and regulations regarding the security and privacy of data. They need to manage information security across their operations by implementing technical and nontechnical controls. EsBank decided to implement an ISMS based on ISO/IEC 27001 because it provided better security, more risk control, and compliance with key requirements of laws and regulations.
Nine months after the successful implementation of the ISMS, EsBank decided to pursue certification of their ISMS by an independent certification body against ISO/IEC 27001 .The certification audit included all of EsBank’s systems, processes, and technologies.
The stage 1 and stage 2 audits were conducted jointly and several nonconformities were detected. The first nonconformity was related to EsBank’s labeling of information. The company had an information classification scheme but there was no information labeling procedure. As a result, documents requiring the same level of protection would be labeled differently (sometimes as confidential, other times sensitive).
Considering that all the documents were also stored electronically, the nonconformity also impacted media handling. The audit team used sampling and concluded that 50 of 200 removable media stored sensitive information mistakenly classified as confidential. According to the information classification scheme, confidential information is allowed to be stored in removable media, whereas storing sensitive information is strictly prohibited. This marked the other nonconformity.
They drafted the nonconformity report and discussed the audit conclusions with EsBank’s representatives, who agreed to submit an action plan for the detected nonconformities within two months.
EsBank accepted the audit team leader's proposed solution. They resolved the nonconformities by drafting a procedure for information labeling based on the classification scheme for both physical and electronic formats. The removable media procedure was also updated based on this procedure.
Two weeks after the audit completion, EsBank submitted a general action plan. There, they addressed the detected nonconformities and the corrective actions taken, but did not include any details on systems, controls, or operations impacted. The audit team evaluated the action plan and concluded that it would resolve the nonconformities. Yet, EsBank received an unfavorable recommendation for certification.
Based on the scenario above, answer the following question:
By drafting a procedure for information labeling, EsBank has:
The audit team leader prepares the audit plan for an initial certification stage 2 audit to ISO/IEC 27001:2022.
Which one of the following statements is true?
The auditor used sampling to ensure that event logs recording information security events are maintained and regularly reviewed. Sampling was based on the audit objectives, whereas the sample selection process was based on the probability theory. What type of sampling was used?
You are an experienced ISMS audit team leader providing guidance to an ISMS auditor in training. They have been asked to carry out an assessment of external providers and have prepared a checklist containing the following activities. They have asked you to review their checklist to confirm that the actions they are proposing are appropriate.
The audit they have been invited to participate in is a third-party surveillance audit of a data centre . The data centre agent is part of a wider telecommunication group. Each data centre within the group operates its own ISMS and holds its own certificate.
Select three options that relate to ISO/IEC 27001:2022's requirements regarding external providers.
Scenario 6: Sinvestment is an insurance company that offers home, commercial, and life insurance. The company was founded in North Carolina, but have recently expanded in other locations, including Europe and Africa.
Sinvestment is committed to complying with laws and regulations applicable to their industry and preventing any information security incident. They have implemented an ISMS based on ISO/IEC 27001 and have applied for ISO/IEC 27001 certification.
Two auditors were assigned by the certification body to conduct the audit. After signing a confidentiality agreement with Sinvestment. they started the audit activities. First, they reviewed the documentation required by the standard, including the declaration of the ISMS scope, information security policies, and internal audits reports. The review process was not easy because, although Sinvestment stated that they had a documentation procedure in place, not all documents had the same format.
Then, the audit team conducted several interviews with Sinvestment's top management to understand their role in the ISMS implementation. All activities of the stage 1 audit were performed remotely, except the review of documented information, which took place on-site, as requested by Sinvestment.
During this stage, the auditors found out that there was no documentation related to information security training and awareness program. When asked, Sinvestment's representatives stated that the company has provided information security training sessions to all employees. Stage 1 audit gave the audit team a general understanding of Sinvestment's operations and ISMS.
The stage 2 audit was conducted three weeks after stage 1 audit. The audit team observed that the marketing department (which was not included in the audit scope) had no procedures in place to control employees’ access rights. Since controlling employees' access rights is one of the ISO/IEC 27001 requirements and was included in the information security policy of the company, the issue was included in the audit report. In addition, during stage 2 audit, the audit team observed that Sinvestment did not record logs of user activities. The procedures of the company stated that "Logs recording user activities should be retained and regularly reviewed," yet the company did not present any evidence of the implementation of such procedure.
During all audit activities, the auditors used observation, interviews, documented information review, analysis, and technical verification to collect information and evidence. All the audit findings during stages 1 and 2 were analyzed and the audit team decided to issue a positive recommendation for certification.
According to scenario 6, the marketing department employees were not following the access control policy. Which option is correct in this case?
Which two options are benefits of third-party accredited certification of information security management systems to ISO/IEC 27001:2022 for organisations and interested parties?
You received an email requiring you to send information such as name, email, and password in order to continue using your email account. If you do not send such
information, your email account will be disabled. What does this scenario present?
You are an experienced ISMS audit team leader providing guidance to an auditor in training.
The auditor in training appears to be confused about the interpretation of competence in ISO 27001:2022 and is seeking clarification from you that his understanding is correct. He sets out a series of mini scenarios and asks you which of these you would attribute to a lack of competence. Select four correct options.
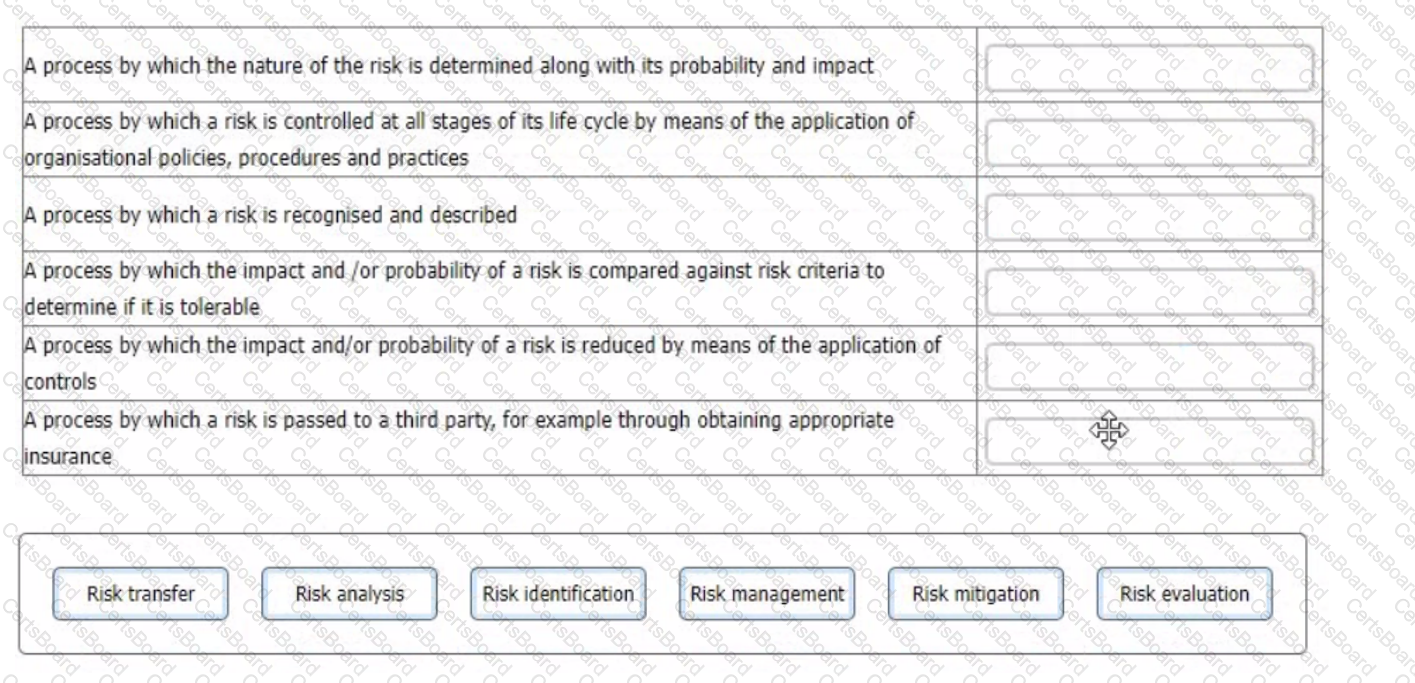
You are an experienced ISMS audit team leader providing instruction to an auditor in training. They are unclear in their understanding of risk processes and ask you to provide them with an example of each of the processes detailed below.
Match each of the descriptions provided to one of the following risk management processes.
To complete the table click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop each option to the appropriate blank section.