How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
Under what conditions does a secondary name server request a zone transfer from a primary name server?
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below:
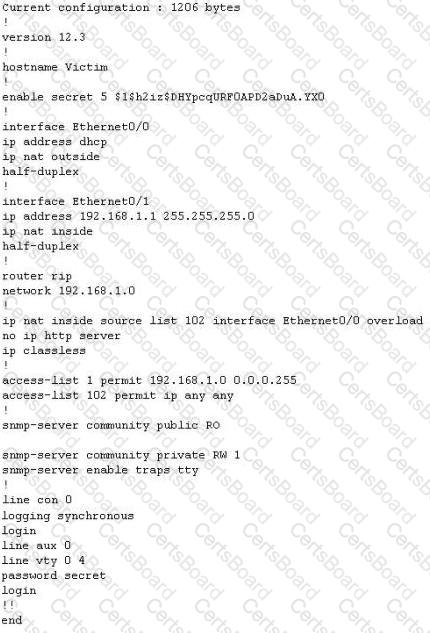
You are hired to conduct security testing on their network. You successfully brute-force the SNMP community string using a SNMP crack tool. The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
Data is sent over the network as clear text (unencrypted) when Basic Authentication is configured on Web Servers.


