What are the roles of 802.1X authenticators and authentication servers?
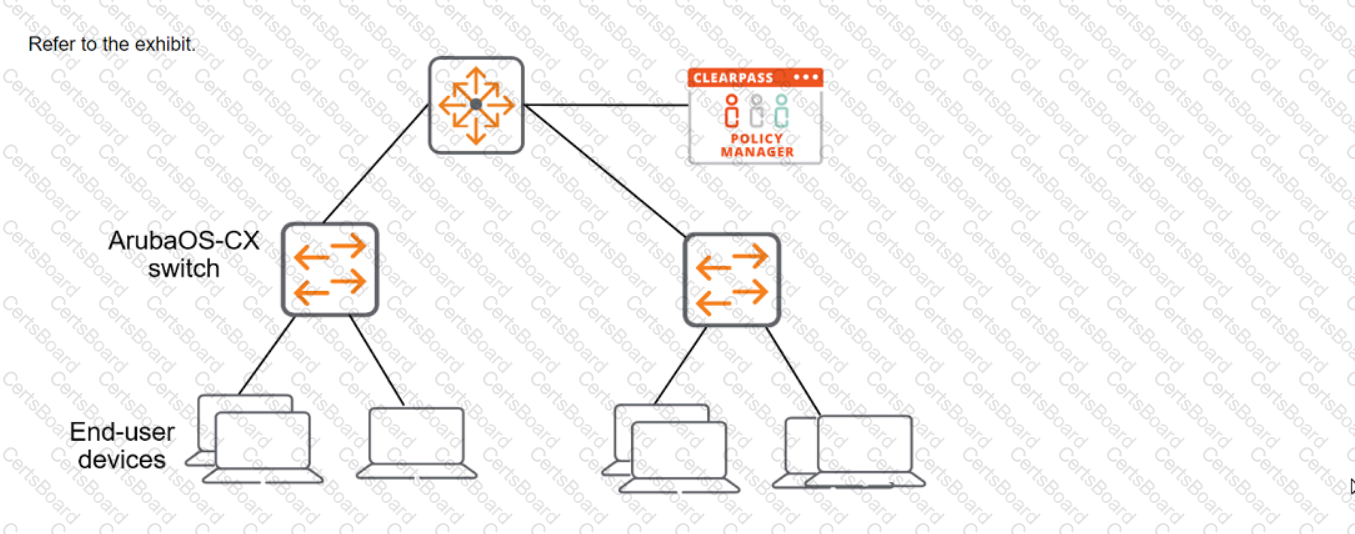
What is another setting that you must configure on the switch to meet these requirements?
What is one difference between EAP-Tunneled Layer security (EAP-TLS) and Protected EAP (PEAP)?
How can hackers implement a man-in-the-middle (MITM) attack against a wireless client?


