Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?
An organization has two systems in their DMZ that have an unencrypted link between them for communication.
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability
would help an attacker brute force their way into the systems?
Drag and drop the solutions from the left onto the solution's benefits on the right.

Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two)
What is the role of Cisco Umbrella Roaming when it is installed on an endpoint?
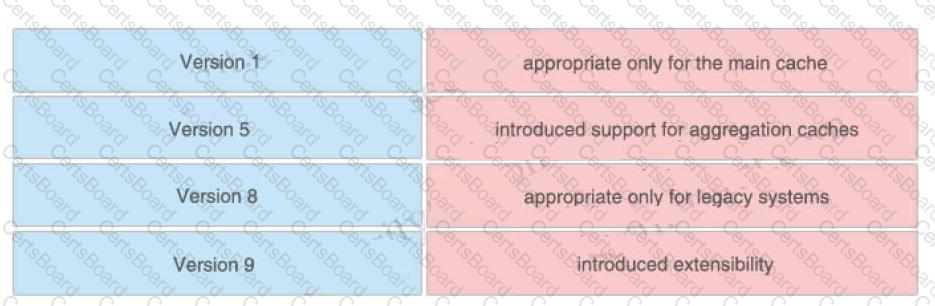
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392368270. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however it is unable to do so. Which command is required to enable the client to accept the server’s authentication key?
An engineer needs a cloud solution that will monitor traffic, create incidents based on events, and integrate with
other cloud solutions via an API. Which solution should be used to accomplish this goal?


