Refer to the exhibit.
What does the output indicate about the server with the IP address 172.18.104.139?
A member of the SOC team is checking the dashboard provided by the Cisco Firepower Manager for further Isolation actions. According to NIST SP800-61, in which phase of incident response is this action?
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
Refer to the exhibit.
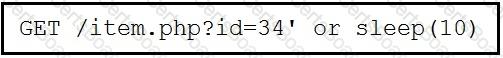
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
Refer to the exhibit.
An attacker scanned the server using Nmap.
What did the attacker obtain from this scan?


