A security analyst wants to better understand the behavior of users and devices in order to gain visibility into potential malicious activities. The analyst needs a control to detect when actions deviate from a common baseline Which of the following should the analyst use?
During a recent log review, an analyst discovers evidence of successful injection attacks. Which of the following will best address this issue?
A company installed cameras and added signs to alert visitors that they are being recorded. Which of the following controls did the company implement? (Select two).
A security analyst reviews domain activity logs and notices the following:
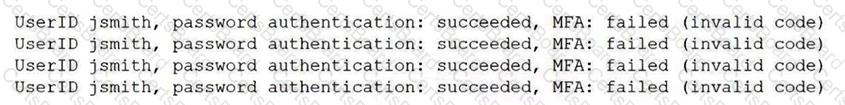
Which of the following is the best explanation for what the security analyst has discovered?
Which of the following techniques can be used to sanitize the data contained on a hard drive while allowing for the hard drive to be repurposed?
Which of the following threat vectors is most commonly utilized by insider threat actors attempting data exfiltration?
A company's online shopping website became unusable shortly after midnight on January 30, 2023. When a security analyst reviewed the database server, the analyst noticed the following code used for backing up data:
Which of the following should the analyst do next?
Which of the following would be most useful in determining whether the long-term cost to transfer a risk is less than the impact of the risk?
A network manager wants to protect the company's VPN by implementing multifactor authentication that uses:
. Something you know
. Something you have
. Something you are
Which of the following would accomplish the manager's goal?
An employee recently resigned from a company. The employee was responsible for managing and supporting weekly batch jobs over the past five years. A few weeks after the employee resigned. one of the batch jobs talked and caused a major disruption. Which of the following would work best to prevent this type of incident from reoccurring?