What happens, by default, when the GlobalProtect app fails to establish an IPSec tunnel to the GlobalProtect gateway?
An engineer troubleshooting a VPN issue needs to manually initiate a VPN tunnel from the CLI Which CLI command can the engineer use?
An administrator wants to configure the Palo Alto Networks Windows User-D agent to map IP addresses to u: ‘The company uses four Microsoft Active ‘servers and two Microsoft Exchange servers, which can provide logs for login events. All six servers have IP addresses assigned from the following subnet: 192.168.28.32/27. The Microsoft Active Directory in 192.168.28.22/128, and the Microsoft Exchange reside in 192,168.28 48/28. What the 0 the User
All firewall at a company are currently forwarding logs to Palo Alto Networks log collectors. The company also wants to deploy a sylog server and forward all firewall logs to the syslog server and to the log collectors. There is known logging peak time during the day, and the security team has asked the firewall engineer to determined how many logs per second the current Palo Alto Networking log processing at that particular time. Which method is the most time-efficient to complete this task?
What would allow a network security administrator to authenticate and identify a user with a new BYOD-type device that is not joined to the corporate domain?
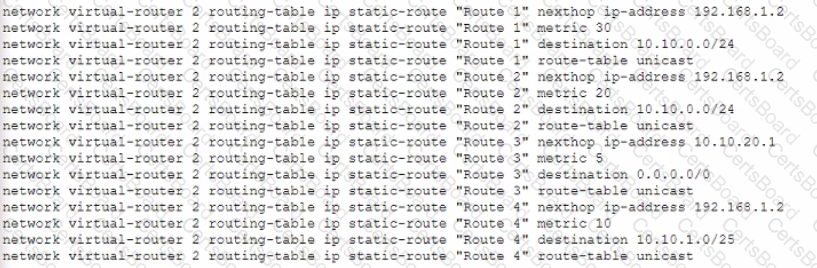
Given the following configuration, which route is used for destination 10 10 0 4?
What are three prerequisites for credential phishing prevention to function? (Choose three.)
A network engineer troubleshoots a VPN Phase 2 mismatch and decides that PFS (Perfect Forward Secrecy) needs to be enabled. What action should the engineer take?
An enterprise network security team is deploying VM-Series firewalls in a multi-cloud environment. Some firewalls are deployed in VMware NSX-V, while others are in AWS, and all are centrally managed using Panorama with the appropriate plugins installed. The team wants to streamline policy management by organizing the firewalls into device groups in which the AWS-based firewalls act as a parent device group, while the NSX-V firewalls are configured as a child device group to inherit Security policies. However, after configuring the device group hierarchy and attempting to push configurations, the team receives errors, and policy inheritance is not functioning as expected. What is the most likely cause of this issue?


