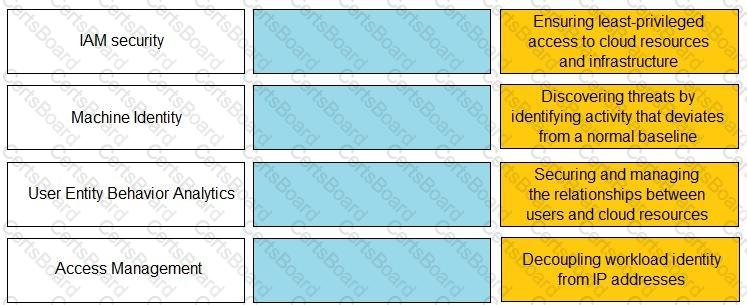
Match the Identity and Access Management (IAM) security control with the appropriate definition.
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
Which not-for-profit organization maintains the common vulnerability exposure catalog that is available through their public website?
Based on how much is managed by the vendor, where can CaaS be situated in the spread of cloud computing services?
Which security component should you configure to block viruses not seen and blocked by the perimeter firewall?
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?


