Which three criteria can a FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
Which three statements explain a flow-based antivirus profile? (Choose three.)
Refer to the exhibit.
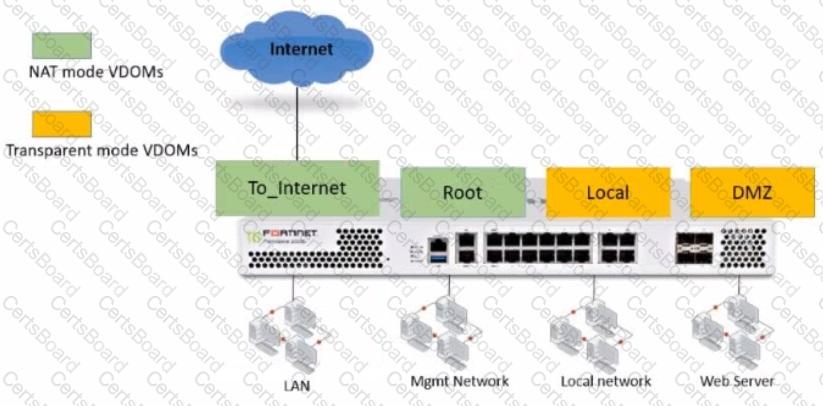
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to ISP modem .
With this configuration, which statement is true?
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
Refer to the exhibits.
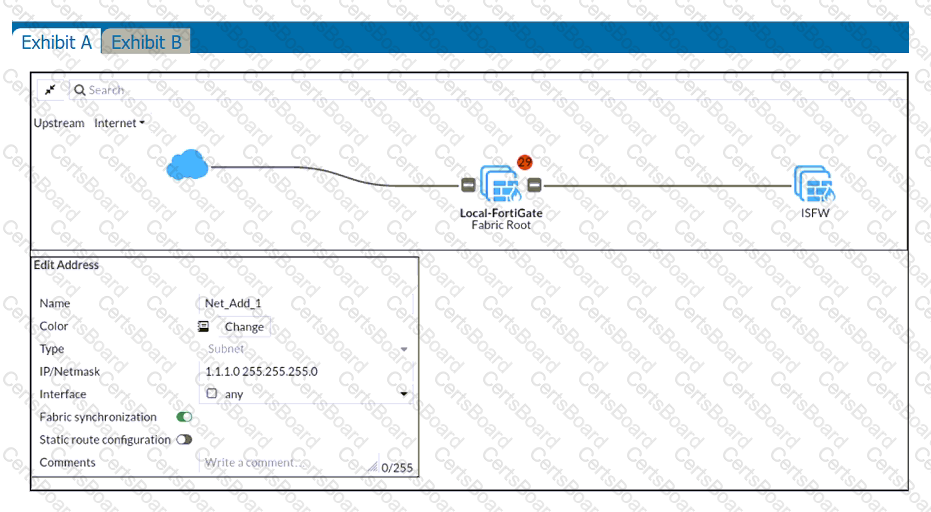
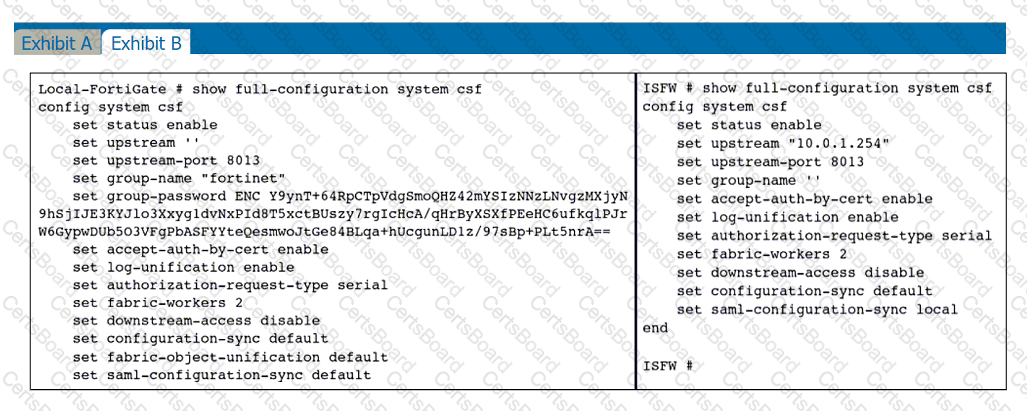
An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).
What must the administrator do to synchronize the address object?
What are two benefits of flow-based inspection compared to proxy-based inspection? (Choose two.)
Which statements about the firmware upgrade process on an active-active HA cluster are true? (Choose two.)
Examine this FortiGate configuration:

How does the FortiGate handle web proxy traffic coming from the IP address 10.2.1.200 that requires authorization?


