An administrator needs to allow wide open access to one particular NC2 AWS cluster from an on-premises subnet of 10.19.160.0/24.
What is the proper Custom Security Group formatting to satisfy this task?
A)
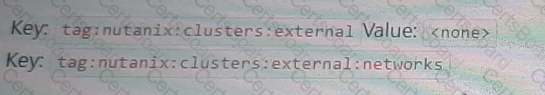
B)
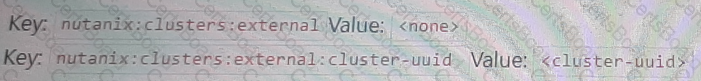
C)
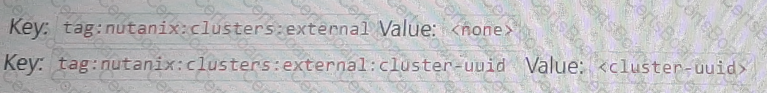
D)
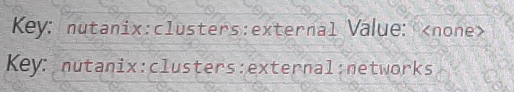
An administrator has created an NC2 cluster on AWS, but the NC2 console has issued this alert:

Which two scenarios could have resulted in the cluster creation failure? (Choose two.)
A company has just adopted Nutanix as their technology of choice and is preparing to deploy Nutanix Cloud Clusters (NC2).
Which step must be taken first to again access to the CN2 console?
Which service enables the monitoring of key metrics on various AWS services, inducing EC2, EBS, and VPC for an NC2 cluster deployments?
An administrator seeks to ensure that the newly created NC2 organization named Finance can only deploy clusters into certain cloud regions.
What action should the administrator take to do this?
An administrator has deployed an NC2 cluster on AWS to an existing environment for VDI.
Afterwards, the corporate security teamsdirectthe administrator to reuse an existing AWS subnet, 10.79.4.0/24 that has two EC2 instances: EC2-1 (10.79.4.200) and EC2-2 (10.79.4.201). The security team indicates that this directive is to avoid overlap with the AHV IPAM.
Which two configuration actions should the administrator take to ensure there are no configuration issues? (Choose two.)
When selecting the NC2 subscription plan from the Nutanix Billing portal, which options are available.
Which two features or services can an administrator ensure are protected by cluster protect within an NC2 environment? (Choose two.)
An administrator has noticed the company’s NC2 free trial expired 60 days ago.
What should the administrator do to continue using all of the NC2 features on existing clusters?


