Comprehensive Detailed Step-by-Step Explanation with All Juniper Security References
Understanding the Problem:
The goal is to bypass IDP for traffic destined to social media sites using Application-Based Policy Routing (APBR).
Despite the configuration, IDP is still dropping the sessions.
Need to identify two reasons why this is happening.
Key Concepts:
Application-Based Policy Routing (APBR): Allows routing decisions based on the application identified in the traffic.
IDP (Intrusion Detection and Prevention): Monitors network traffic for malicious activity and can drop suspicious packets.
Bypassing IDP: To bypass IDP for certain traffic, specific configurations are required within the APBR rule.
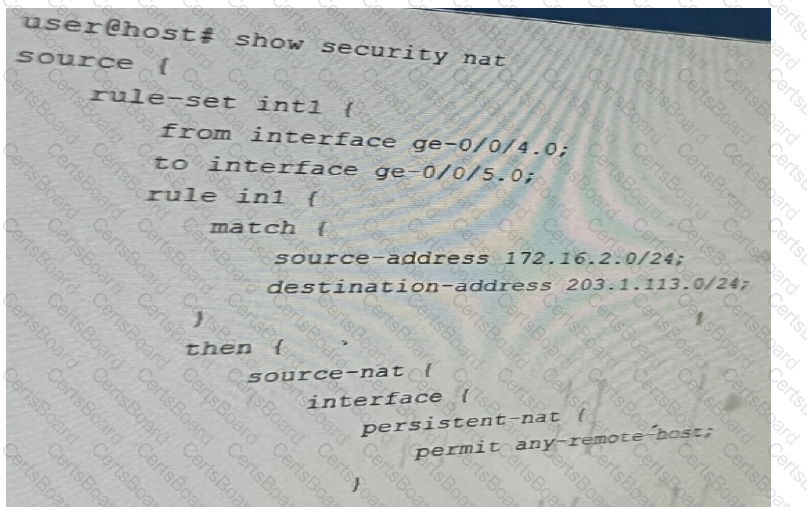
Option A: IDP disable is not configured on the APBR rule.
Explanation:
To bypass IDP for specific traffic using APBR, you must explicitly configure the idp-disable option within the APBR rule.
Without this configuration, even if APBR redirects the traffic, IDP will still inspect and potentially drop the traffic.
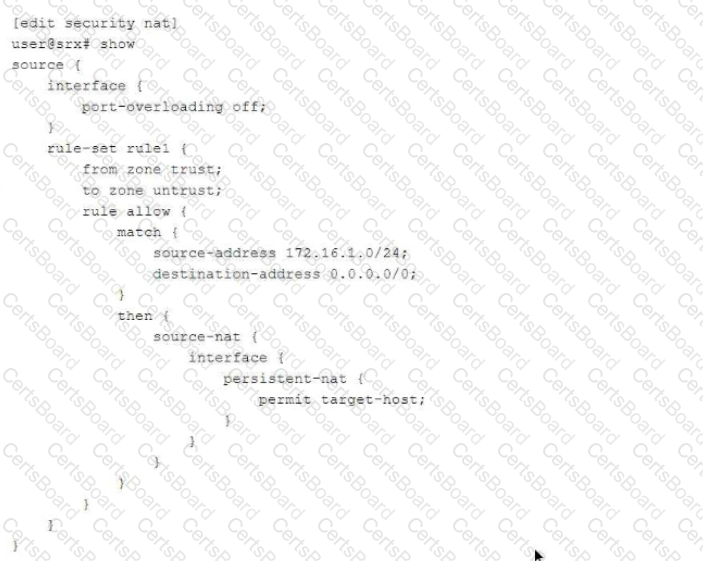
[Reference:, Juniper Networks Documentation:, "To bypass IDP processing for traffic matching an APBR rule, include the idp-disable statement in the rule configuration.", Source: Juniper TechLibrary - Configuring APBR to Bypass IDP, , Option D: The session did not properly reclassify midstream to the correct APBR rule., Explanation:, Midstream Reclassification: APBR relies on application identification, which may occur after several packets have been exchanged (not just the first packet)., When the application is identified mid-session, the session should be reclassified according to the correct APBR rule., If midstream reclassification does not occur properly, the session continues under the initial policy, and IDP continues to inspect and potentially drop the traffic., Possible Causes:, Session Setup Issues: If the session was established before the application was identified, and reclassification is not enabled or not functioning, the session won't switch to the APBR rule that bypasses IDP., Configuration Errors: Incorrect or missing configuration for midstream reclassification., Reference:, Juniper Networks Documentation:, "For APBR to reclassify sessions after the application is identified, ensure that midstream reclassification is enabled.", Source: Juniper TechLibrary - Understanding APBR and Midstream Reclassification, , Why Options B and C are Incorrect:, Option B: The application services bypass is not configured on the APBR rule., Explanation:, There is no specific application-services bypass option within APBR rules for bypassing IDP., To bypass IDP, the idp-disable option must be used., Application services bypass generally refers to bypassing other services like UTM, not specifically IDP within APBR., Reference:, Juniper Networks Documentation:, "APBR rules can include the idp-disable statement to bypass IDP. There is no application-services bypass statement for APBR.", Option C: The APBR rule does a match on the first packet., Explanation:, By default, APBR can match on the first packet, but for applications that require deeper inspection, you can configure the rule to not match on the first packet., Matching on the first packet is generally beneficial for routing decisions., In this scenario, matching on the first packet is not the reason why IDP is dropping the session., Reference:, Juniper Networks Documentation:, "If you configure APBR to match on the first packet, the routing decision is made immediately. If the application is not identified on the first packet, the default routing is used until the application is identified.", , Conclusion:, Correct Answers:, A. IDP disable is not configured on the APBR rule., Without idp-disable, IDP will continue to inspect and possibly drop the traffic matching the APBR rule., D. The session did not properly reclassify midstream to the correct APBR rule., If midstream reclassification fails, the session remains under the initial policy, and IDP processing continues., Resolution Steps:, Configure idp-disable: Ensure that the APBR rule includes the idp-disable statement to bypass IDP for the specified traffic., arduino, Copy code, set security application-path-routing rule then idp-disable, Enable Midstream Reclassification: Verify that midstream reclassification is enabled and functioning correctly to reclassify sessions once the application is identified., Note: Midstream reclassification is enabled by default, but verify that no configuration is preventing it., , Additional References:, Juniper TechLibrary:, "Application-Based Policy Routing Overview" - Provides an overview of APBR features and configurations., Source: Juniper TechLibrary - APBR Overview, "Configuring IDP Policy Bypass" - Discusses how to bypass IDP for specific traffic., Source: Juniper TechLibrary - Configuring IDP Bypass, Juniper Networks Day One Book:, "Advanced Security Policies" - Offers insights into configuring advanced security policies, including APBR and IDP interactions., ]