In which of the following alternative processing sites is the backup facility maintained in a constant order, with a full complement of servers, workstations, and communication links ready to assume the primary operations responsibility?
Which of the following administrative policy controls is usually associated with government classifications of materials and the clearances of individuals to access those materials?
Which of the following methods for identifying appropriate BIA interviewees' includes examining the organizational chart of the enterprise to understand the functional positions?
Which of the following statements best explains how encryption works on the Internet?
You are the project manager of the GHE Project. You have identified the following risks with the characteristics as shown in the following figure:
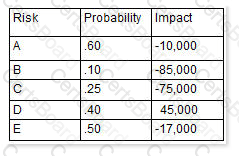
How much capital should the project set aside for the risk contingency reserve?
Which of the following evidences are the collection of facts that, when considered together, can be used to infer a conclusion about the malicious activity/person?
You are the Network Administrator for a software company. Due to the nature of your company's business, you have a significant number of highly computer savvy users. However, you have still decided to limit each user access to only those resources required for their job, rather than give wider access to the technical users (such as tech support and software engineering personnel). What is this an example of?
Rick is the project manager for TTM project. He is in the process of procuring services from vendors. He makes a contract with a vendor in which he precisely specify the services to be procured, and any changes to the procurement specification will increase the costs to the buyer. Which type of contract is this?
Which of the following are the types of access controls? Each correct answer represents a complete solution. Choose three.


