A network administrator creates an employee WLAN on an Aruba solution that uses WLAN WPA2-Enterprise security and an external RADIUS server. When the administrator tests the WLAN, the test client receives limited connectivity and cannot access any resources, but the RADIUS server shows that the user authenticated successfully.
What should the administrator check as a possible source of this issue?
How can network administrators upgrade AirMatch on an Aruba Mobility Master (MM)?
A company has a Mobility Master (MM)-based solution with an employee WLAN Several users report that they can connect to the WLAN, but they cannot access all of the resources that they should.
Where should the network administrator look in the MM interface to find the roles to which these users are actually assigned?
An Aruba Mobility Master (MM)-based solution has a WLAN that uses WPA2-Enterprise security. A test login on a wireless client fails.
How can a network administrator determine whether the RADIUS server rejected the credentials or another issue occurred?
A network administrator uses a wireless intrusion detection system (WIDS) to detect 802.11 association floods. At which layer do these attacks occur?
A network administrator configures an Aruba Mobility Master (MM)-based solution to provide wireless access to employees. The solution must meet these criteria:
How can the administrator meet these criteria in the simplest way?
A company has a single Aruba Mobility Master (MM)-based solution with two Mobility Controllers (MCs). Network administrators want APs in building 1 to support a WLAN but do not want APs in building 2 to support the WLAN.
How can administrator ensure that they can enforce this rule as they set up the WLAN in the Mobility Master (MM) Interface?
Refer to the exhibit.
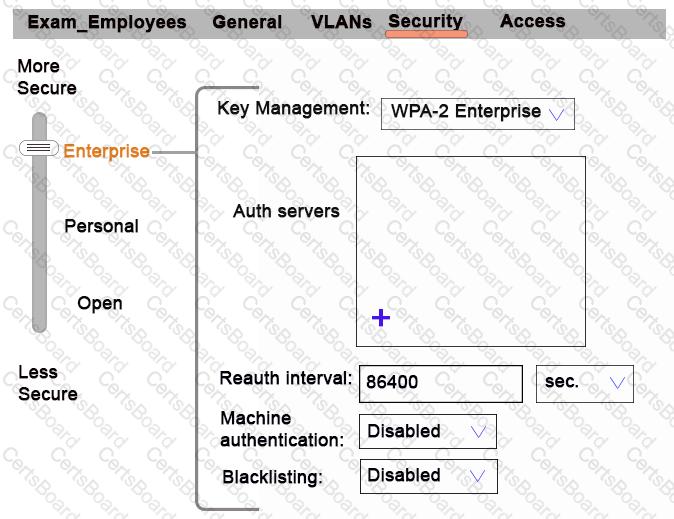
Network administrators need to set up a WLAN that uses WPA2 encryption and authenticates users with a preshared key (PSK) that is the same for all users. Administrators do not see where they should specify the option for the preshared key.
What should the administrators do?
A company has a Mobility Master (MM)-based solution. How does a Mobility Controller (MC) behave if it loses contact with all MM nodes?


