Which of the following statements aboutSR-MPLS Policy path planningare correct?
Which of the following statements are correct about the authentication protocols used inPortal authentication?
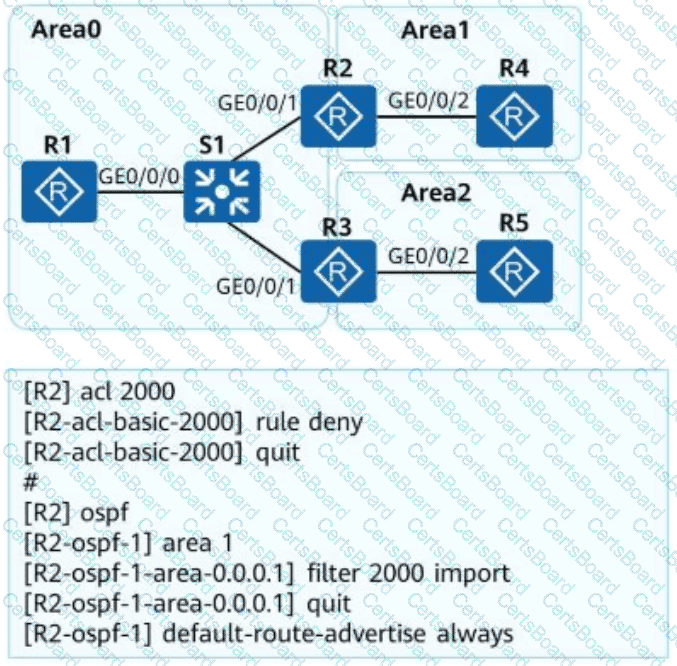
OSPF is deployed on a campus network to implement network interconnection. An engineer configures R2 as shown in the figure. Which of the following statements is incorrect about LSAs on the OSPF network?
An engineer uses two routers to perform IPv6 tests and wants to use OSPFv3 for IPv6 network connectivity. Which of the following OSPFv3 configurations for R1 are correct?
Which of the following inter-AS MPLS L3VPN solutions need VPN user data packets to carry MPLS labels when being forwarded between ASs?
When you configure a virtualized campus network on iMaster NCE-Campus and enable external networks to connect to the Internet, iMaster NCE-Campus will automatically deliver a specific route to direct traffic to the corresponding external network.
If ISIS is used to transmit SIDs on an SR network, the node SIDs advertised by a Level-2 router are transmitted only within the same area.
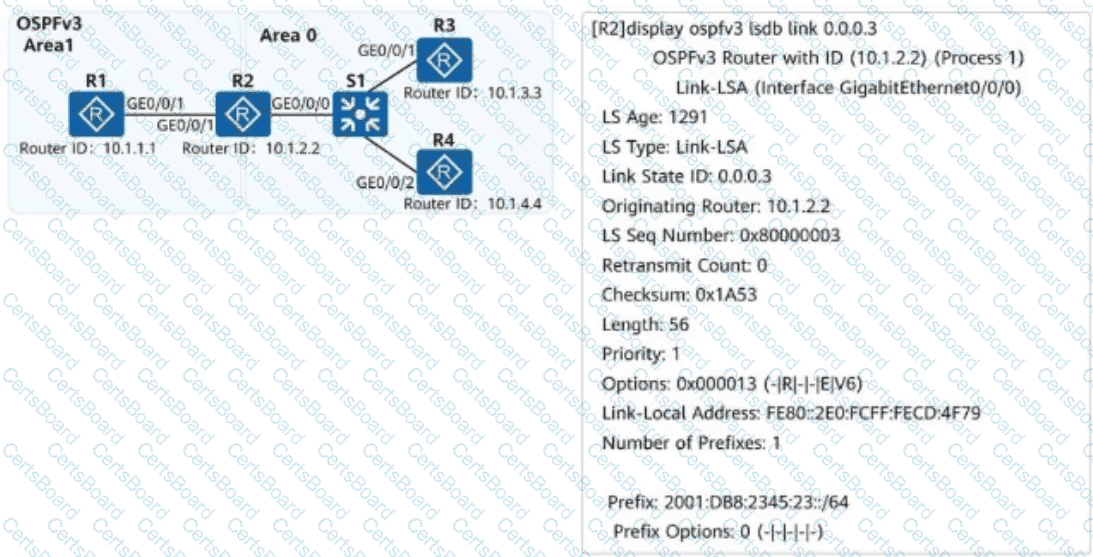
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and OSPFv3 is used for IPv6 network connectivity. An engineer checks the LSDB of R2 and obtains a Link-LSA. Which of the following statements about the LSA are correct?
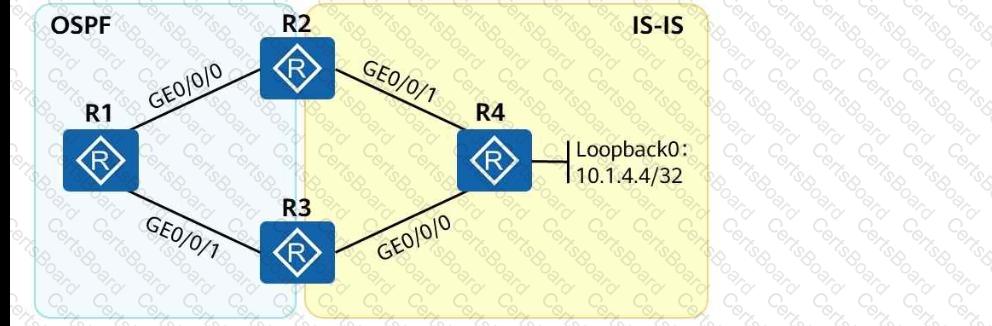
As shown in the following figure, an engineer tests network interconnection between two branches. To implement network interconnection,OSPFis deployed onR1, R2, and R3of branch 1, andIS-ISis deployed onR2, R3, and R4of branch 2. Which of the following operations needs to be performed to allowR1 to access R4's loopback interface address?
Drag the authentication modes on the left into their applicable scenarios on the right.
