Which of the following statements is false about hot standby networking?(Select All that Apply)
HWTACACS is a centralized information exchange protocol based on the client/server structure. It uses UDP for transmission and performs authentication, authorization, and accounting for users accessing the Internet through Point-to-Point Protocol (PPP) or Virtual Private Dial-up Network (VPDN) and administrative users logging in to devices.
In a Huawei network security environment, which of the following is a key advantage of using HWTACACS over RADIUS for device management authentication?
Options:
Which of the following statements is false about virtual system resource allocation?
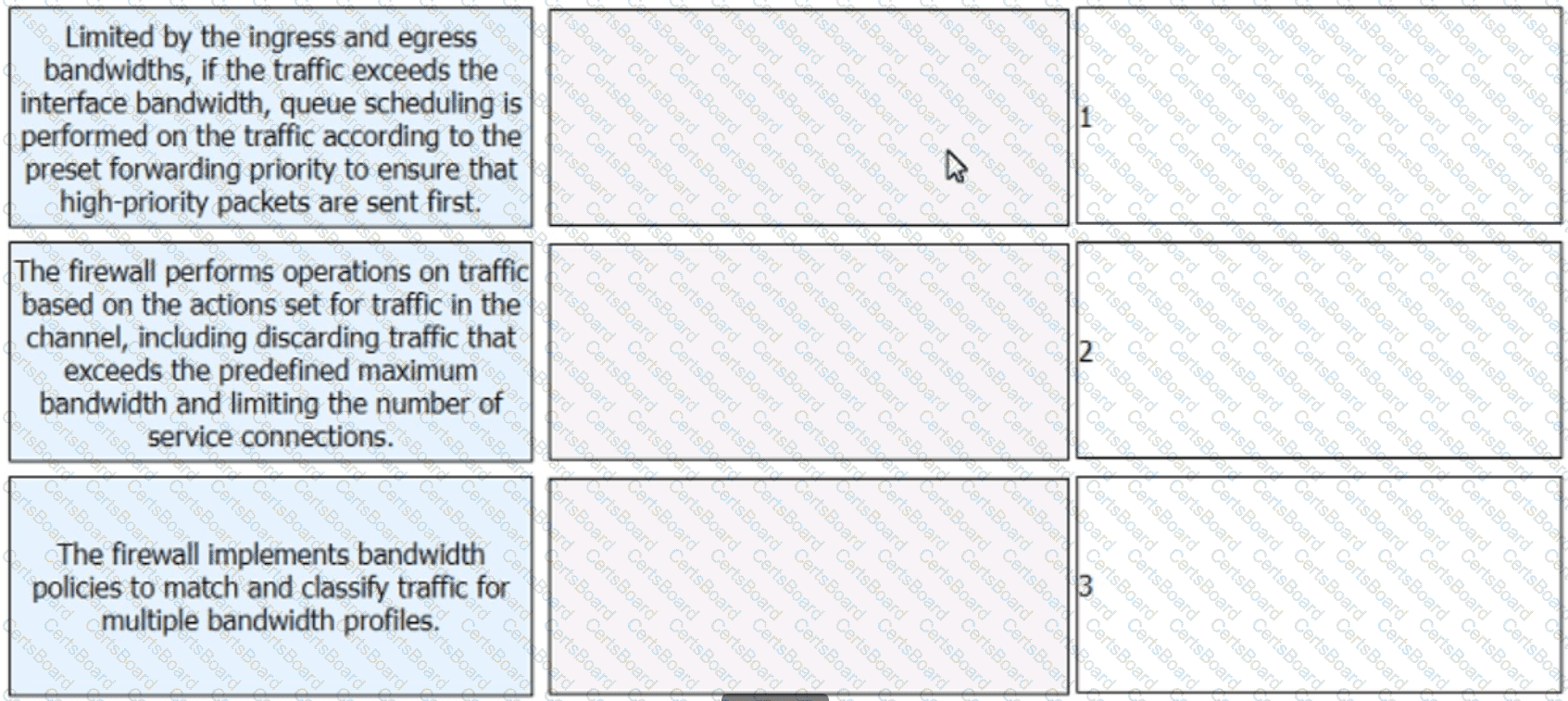
: 52 DRAG DROP
Arrange the steps of the bandwidth management process on firewalls in the correct sequence.
On a WLAN where the WAC has Portal authentication configured, VLAN authorization can be implemented with no additional configuration required. After Portal authentication is complete, the WAC forwards STA traffic based on the authorized VLANs.
Which of the following is not a process for remote users to access intranet resources through SSL VPN?
Which of the following statements is true about the incoming traffic in the firewall virtualsystem?(Select All that Apply)